Implement an authentication and access management solution
- By Razi Rais, Jeevan Bisht, Padma Chilakapati, Ilya Lushnikov, Vinayak Shenoy
- 6/26/2023
- Skill 2.1: Plan, implement, and manage Azure Multifactor Authentication (MFA) and self-service password reset
- Skill 2.2: Plan, implement, and manage Azure AD user authentication
Skill 2.2: Plan, implement, and manage Azure AD user authentication
When a user signs in to a device, application, or service, one of the primary functions of an Azure AD is to authenticate credentials. However, in Azure AD, there are multiple options for user authentication that go beyond simply verifying a username and password and provide a range of security protections such as phishing resistance, biometrics, and so on.
Plan for authentication
Planning for authentication is an important part of determining which method provides the best combination of usability and security. Traditionally, username and password is the most popular authentication method used to verify user credentials. However, it is also the least secure method because it is easy to launch a brute force attack against the passwords. To improve security, it is highly recommended to replace the password or at least use an additional authentication method for sign-ins. Azure AD provides a range of passwordless MFA methods to the users.
Users can use Azure AD passwordless authentication methods such as FIDO2 security keys, Windows Hello for Business, and the Microsoft Authenticator app during sign-ins.
Table 2-5 provides a summary of various authentication methods that can be used for sign-ins. Please note that some of these methods can be used for both MFA and self-service password reset (SSPR). (SSPR is covered in a later section.)
TABLE 2-5 Azure AD authentication methods and usage.
Authentication method |
Usage |
Password |
Azure AD MFA and SSPR |
Microsoft Authenticator app |
Azure AD MFA and SSPR Available to users using iOS and Android operating system. Users may register their mobile app at https://aka.ms/mfasetup. By using the Microsoft Authenticator app, users receive push notifications on their smartphone or tablet and then reject or approve the request. Users can also use the Microsoft Authentication app to generate an OATH verification code. During the sign-in process, this verification code can be used as a second form of authentication. |
Voice call |
Azure AD MFA and SSPR Voice call is placed by the Azure automated voice system to the user’s phone number. The user receives the call and then must use a keypad to confirm or deny the authentication. |
Text messages |
Azure AD MFA and SSPR A text message containing a time-bound verification code is sent by Azure MFA via SMS to the user’s mobile phone. The user must enter this verification code during the sign-in process within the specific time period to complete the verification process. |
FIDO2 Security Key |
Azure AD MFA and SSPR Fast Identity Online (FIDO) is an open standard for passwordless authentication. The user first needs to register a FIDO2 security key and then select it at the time of sign-in for authentication purposes. FIDO2 security keys are available in the form of USB devices, Bluetooth, and NFC. |
Windows Hello for Business |
Azure AD MFA and SSPR Windows Hello for Business (WHfB)is a fully integrated biometric authentication method based on facial recognition or fingerprint matching. Users need Windows 10 or a later version of the Windows operating system to use WHfB to sign in to Azure Active Directory. |
OATH software token |
Azure AD MFA and SSPR Users can use the Microsoft Authenticator app or other similar authenticator apps that can generate software-based OATH tokens to sign in to Azure Active Directory. |
OATH hardware token |
Azure AD MFA and SSPR OATH is an open standard to generate one-time password (OTP) verification codes. Azure Active Directory natively supports hardware-based OATH time-based one-time password SHA-1 tokens with 30 seconds or 60 seconds validity. Users can use hardware devices from their preferred vendors, which are compatible with OATH standards to generate OTPs and use them to sign in to Azure Active Directory. |
Implement and manage authentication methods
As part of the Azure AD sign-in experience, basic password-based authentication should be supplemented or replaced with a more secure authentication method such as FIDO.
Working with FIDO2
The Fast IDentity Online (FIDO) Alliance’s goal is to replace passwords with strong passwordless authentication that is both secure and usable. The latest version of the open specification for passwordless authentication, FIDO2, incorporates the W3C Web Authentication (WebAuthn) standard as well as the FIDO Client to Authenticator Protocol 2 (CTAP2). Users can sign in using an unphishable FIDO2 security key stored in a hardware device that can be accessed via commonly used protocols such as NFC (near-field communication), Bluetooth, and USB.
FIDO2 security keys can be used to sign in to Azure AD or hybrid Azure AD-joined devices to achieve single-sign-on to cloud and on-premises resources.
Enabling the FIDO2 security key method
To enable the FIDO2 security key method for Azure AD:
Sign in as an administrator to the Azure portal at http://portal.azure.com.
Navigate to Azure Active Directory.
Select Security from the left pane, as shown in Figure 2-20.
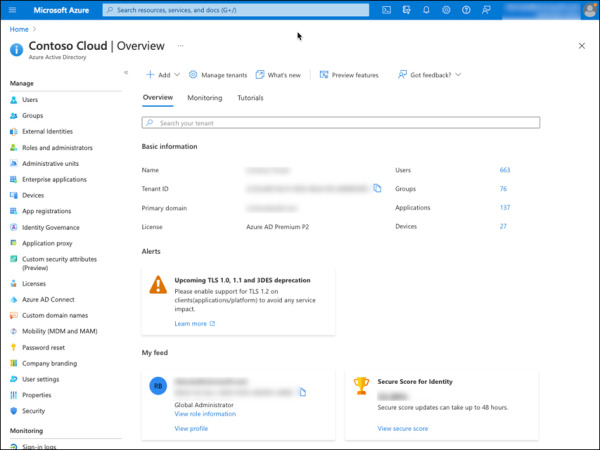
FIGURE 2-20 Azure AD home page with Security option.
Select Authentication methods from the left pane, as shown in Figure 2-21.
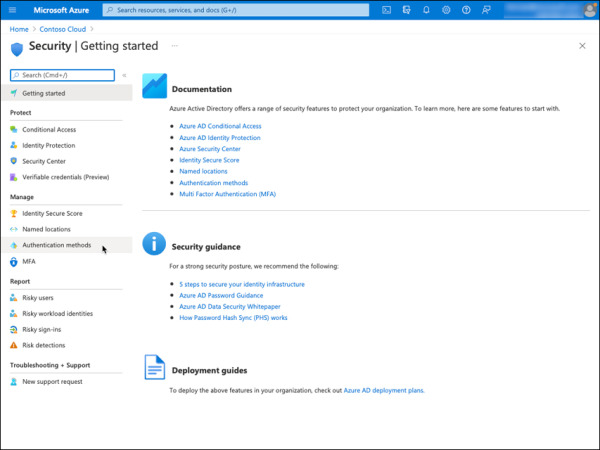
FIGURE 2-21 Azure AD Security settings with the Authentication methods option.
Select FIDO2 Security Key from the list of available methods, as shown in Figure 2-22.
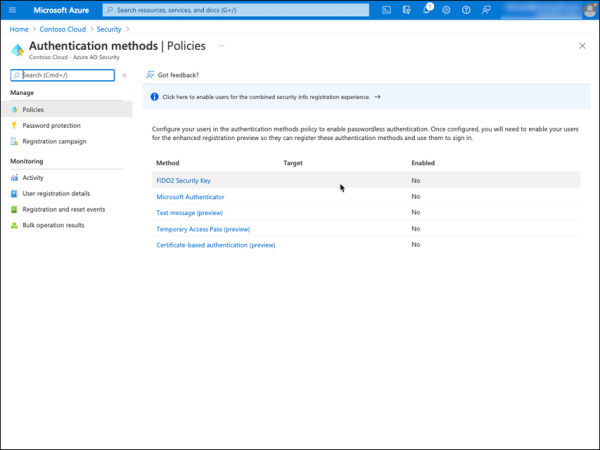
FIGURE 2-22 Azure AD Authentication methods.
Under the Basics tab, choose the following options, as shown in Figure 2-23.
Enable: Yes
Target: All users
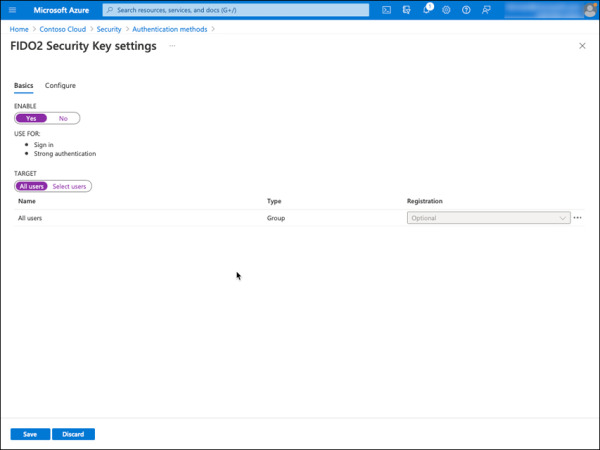
FIGURE 2-23 Azure AD FIDO2 Security Key settings.
Under the Configure tab, choose following options, as shown in Figure 2-24.
Allow self-service set up: Yes
Enforce attestation: No (Default)
Enforce key restrictions: No (Default)
Restrict specific keys: Block (Default)
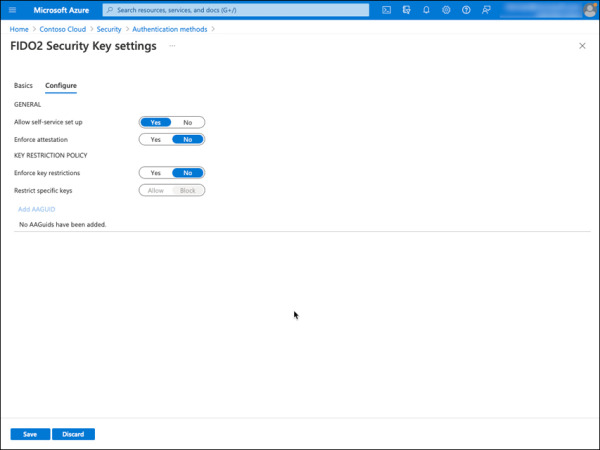
FIGURE 2-24 Azure AD FIDO2 Security Key configuration options.
Click Save.
Register a FIDO2 security key
The user must configure a FIDO2 security key using the steps below before it can be used for sign-in:
Navigate to the URL https://myprofile.microsoft.com/.
Sign in with the user account for which FIDO2 security key needs to be configured.
Select Security info, as shown in Figure 2-25. Make sure there is at least one Azure AD MFA method already registered; otherwise, you must first register for an MFA method before you can register a FIDO2 security key.
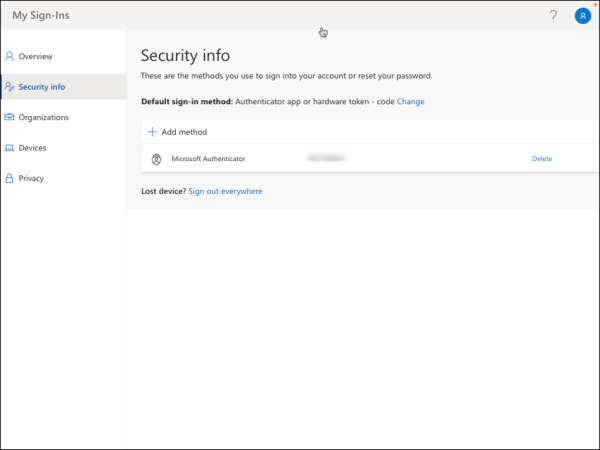
FIGURE 2-25 My Sign-Ins Security info.
Select Security key from the dropdown and click Add, as shown in Figure 2-26.
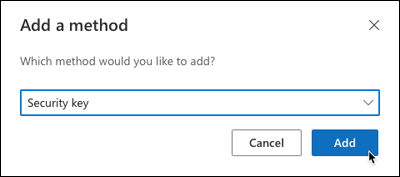
FIGURE 2-26 Adding a security key as an authentication method.
Choose the type of security key, USB device or NFC device, that you would like to use, as shown in Figure 2-27.
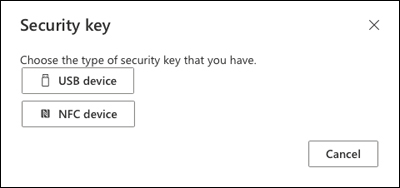
FIGURE 2-27 Security key type selection screen.
Complete the registration process by creating or using a PIN for the security key and then perform a biometric or touch for the gesture.
Provide a meaningful name for the key and select Next.
Finally, select Done to finish the process.
Sign in with passwordless credentials using a FIDO2 security key
The steps below demonstrate how to sign in with passwordless credentials using a FIDO2 security key.
Sign in to the Azure portal at https://portal.azure.com/ using the account for which a FIDO2 security key is already registered.
Complete the sign-in process by providing the security key. For example, Figure 2-28 shows the pop-up message presented by the browser asking a user who has previously registered the security key using a USB device to use it to finish the authentication process.
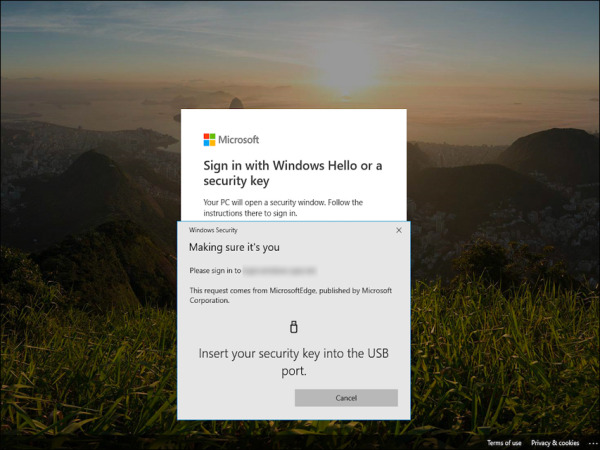
FIGURE 2-28 Sign-in process with security key.
After the successful passwordless authentication using the security key, the user will be taken to the Azure portal (https://portal.azure.com), as shown in Figure 2-29.
FIGURE 2-29 The Azure portal.

 EXAM TIP
EXAM TIP