Design a security operations strategy
- By Yuri Diogenes, Gladys Rodriguez, Mark Simos, Sarah Young
- 6/26/2023
- Skill 2-1: Design a logging and auditing strategy to support security operations
- Skill 2-2: Develop security operations to support a hybrid or multi-cloud environment
Skill 2-2: Develop security operations to support a hybrid or multi-cloud environment
It may seem obvious, but security operations need to cover an organization’s entire IT environment, end to end. Malicious actors look for blind spots and gaps in monitoring and remediation that they can use in order to evade detection. Of course, having security operations cover your entire environment—which has always been challenging—has become even more difficult since an organization’s IT environment stopped being solely in an organization’s datacenter. This section of the chapter covers the skills necessary to develop security operations to support a hybrid or multi-cloud environment according to the Exam SC-100 outline.
Cross-platform log collection
As discussed in Skill 2-1, log collection is a key foundation of a strong security operations function. In modern environments, this has become even more challenging. Not only do you have to decide what logs you need to collect that have security value, but those logs need to be extracted from a wide variety of places ranging from your own on-premises datacenter to a public cloud (or clouds) to a SaaS platform and collected into a centralized SIEM function. It is also rare/impossible that the logs will all be collected in the same manner, so you need to use tooling that can support log collection in different formats.
In a modern cloud-based SIEM like Microsoft Sentinel, collecting logs from multiple sources was considered when building the product. Hundreds of sources are provided for out-of-the-box solutions—including other public clouds such as AWS and GCP—that can be deployed at the click of a button through the Content Hub, as shown in Figure 2-4.
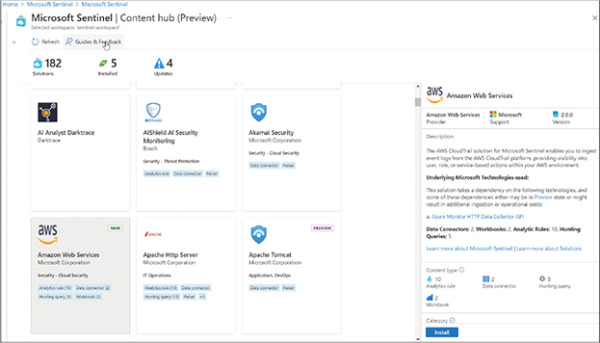
FIGURE 2-4 Searching for solutions in the Microsoft Sentinel Content Hub
Even Microsoft can’t provide solutions to every potential data source out there, so Microsoft Sentinel includes several generic methods of data collection to cover data sources that may not have an out-of-the-box solution:
Log Analytics agent (LA agent) for Windows This agent can collect Windows Security Events and send them to a Log Analytics workspace from any machine on which it is installed, whether on-premises or in the cloud.
Log Analytics agent for Linux (also known as the OMS agent) This agent can centralize syslog and Common Event Format (CEF) logs from any host that generates them and send them to a Log Analytics workspace, whether on-premises or in the cloud.
Azure Monitor Agent (AMA) This is the latest version of Microsoft’s log collection agent and is available for both Windows and Linux. Eventually, it will completely replace the LA agent. AMA supports the same log collection methods as the LA agent and provides enhanced capabilities for filtering logs before they are sent into a Log Analytics/Microsoft Sentinel workspace.
Codeless connector platform (CCP) This platform allows partners and developers to create custom data connectors for Microsoft Sentinel using an API connection. Connectors made using CCP are fully SaaS-based.
Many options and methods are available for bringing logs into a SIEM from all corners of your environment for effective detection and response.
Cloud security posture management (CSPM)
Although it has “cloud” in the title of its name, CSPM isn’t just for cloud-based entities. CSPM tools are tools that monitor the security posture of an entity and will give recommendations based on best practices and industry standards about how to increase the security posture of said entity.
It may not sound particularly exciting or sexy, but research shows that misconfiguration is one of the leading—if not the leading—causes of breaches. Malicious actors look for misconfigurations to exploit—and they often find them. Typically, a misconfiguration is a minor and easy-to-fix problem that has been previously overlooked for some reason. For example, a virtual machine (VM) with port 23—Telnet—left open to the Internet will be found within seconds by port scanners that malicious actors are constantly running. If anyone in your organization tries to log in to that machine via Telnet, it is easy to intercept the username and password. Those credentials could subsequently be used elsewhere in your environment. This might seem like a basic example, but the reality is that misconfiguration happens all the time, whether it be intentional, accidental, or through a lack of knowledge. And it causes breaches.
Microsoft’s CSPM tool is Defender for Cloud (previously known as Azure Security Center) and covers both Infrastructure as a Service (IaaS) and Platform as a Service (PaaS). For VMs, it can be installed on hosts in Azure, AWS, GCP, and on-premises. Even if you have legacy VMs on-premises, it doesn’t mean they can’t benefit from the tooling now powered by the cloud. Defender for Cloud security posture feature provides a grouped list of security posture improvement recommendations, as shown in Figure 2-5.
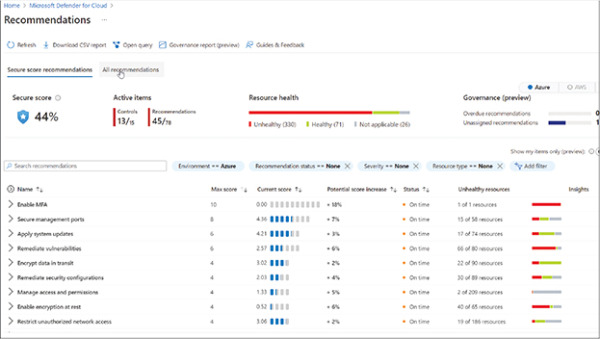
FIGURE 2-5 Checking security posture recommendations in Defender for Cloud
You can drill into these recommendations to see each individual recommended change, as shown Figure 2-6.
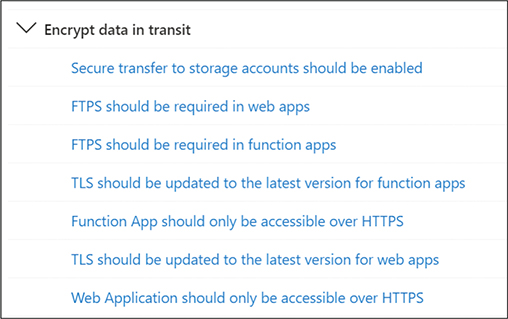
FIGURE 2-6 Drilling into the grouped security posture recommendations in Defender for Cloud
These recommendations can be automatically remediated or manually actioned by your SOC team (or whatever team takes responsibility for this). Sometimes, configuration changes will be actioned outside the SOC. By enabling CSPM across your entire IT environment, you can ensure that configurations stay consistent and secure and reduce your risk of a misconfiguration causing a breach. Alerts from a CSPM tool can also be integrated into a SIEM so the SOC team can act if a high-risk misconfiguration is detected. We discuss posture management using Defender for Cloud in more depth in Chapter 5.
Focus on identity
You may have already heard the phrase “identity is the new perimeter” when discussing cloud and hybrid IT environments. In modern IT environments, identity is our perimeter rather than the traditional network. The most effective way to modernize your security operations and enable identity across different clouds and platforms is to focus on prevention, detection, and response for identities rather than networks. Network-based detections can’t pick up on devices not connected to your internal network. Especially in this post-COVID-19 era, think about how many devices are connected to your internal network versus an external one. Most of you reading this will likely agree that there are far more external than internal!
Identities are the most effective way to track user activity across multiple platforms, clouds, and hybrid environments. Several Microsoft security tools can assist with monitoring identities:
Microsoft Entra This suite of products includes Azure Active Directory, Microsoft Entra Permissions Management, and Microsoft Entra Verified ID. Entra Permissions Management is a cloud infrastructure entitlement management (CIEM) solution that facilitates the management and monitoring of permissions entitlement across different cloud platforms.
Microsoft Identity Protection This tool incorporates all of Microsoft’s identity risk learnings gathered from all the cloud platforms that Microsoft runs (Azure, Xbox, and so on) and uses this information to highlight risks in your identity setup. It can automatically remediate these risks and export the alerts to a SIEM for correlation with other data sources.
Azure AD sign-in logs and audit logs If I was asked to provide a top ten list of the logs that I recommended that people ingested into their SIEM, this would be at the top. It’s critical that you can correlate sign-in and audit logs with other data sources to flush out anomalies and—assuming that you have a centralized identity provider—this is how SOC analysts can track activity that is likely to be tied to one user, even if they are moving across clouds and different platforms.
Internet of Things (IoT) / Operational Technology (OT) coverage
IoT/OT environments can be quite different in how they can be monitored compared to the rest of an IT environment, so it’s worth calling this out as part of multi-platform, modern security operations. Traditionally, IoT/OT environments were not monitored or sparingly monitored. There were a few reasons for this:
Inability to install monitoring on IoT devices Many IoT devices run rudimentary OSs that cannot have additional software or functionality installed on them, which can severely hinder monitoring efforts.
Proprietary protocols Many IoT/OT technologies use proprietary protocols that cannot talk to a standard IT environment, so they are often left alone from a monitoring perspective because it is too hard and/or not worth the effort to integrate them into the wider security operations function.
Air-gapped environments Some IoT/OT environments are completely air-gapped, which makes monitoring challenging or impossible with older monitoring technologies.
Limited use of IoT/OT outside specialized industries About ten years ago, IoT/OT environments only existed for certain industry verticals such as manufacturing.
Many of these challenges still exist with regard to monitoring an IoT/OT environment. The explosion of IoT technologies and several high-profile breaches of IoT/OT environments have made it harder for organizations to simply ignore the IoT environment.
Because of these challenges, specialized security tools for IoT/OT environments are necessary for managing and monitoring devices in these environments. Defender for IoT is a unified security solution for identifying IoT and OT devices, vulnerabilities, and threats and managing them through a central interface. As with all good security tools, the alerts it generates can be exported to a SIEM solution to gain further correlation and visibility across your entire IT environment.
