Azure Sentinel - An Introduction
- By Yuri Diogenes, Nicholas DiCola, Jonathan Trull
- 3/17/2020
Data ingestion
Azure Sentinel enables you to use data connectors to configure connections with different Microsoft services, partner solutions, and other resources. There are several out-of-the-box data connectors available in Azure Sentinel, and there are different ways to ingest data when a connector is not available. Figure 2-7 shows a diagram of the available options.
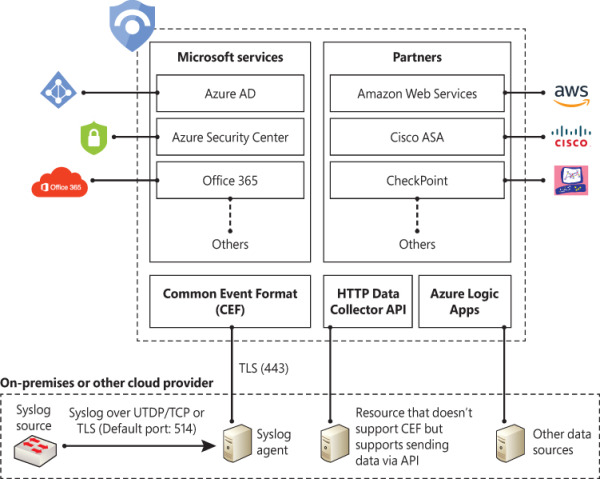
FIGURE 2-7 Different methods to ingest data into Azure Sentinel
Figure 2-7 only shows a small subset of Microsoft services. At the time this chapter was written, Azure Sentinel provided support for the following Microsoft services:
Azure AD
Office 365
Cloud App Security
Azure Activity Log
Azure AD Identity Protection
Azure Information Protection
Azure ATP
Azure Security Center
Domain Name Server
Microsoft Defender ATP
Microsoft Web Application Firewall
Windows Firewall
Windows Security Events
The diagram also shows a subset of partners’ connectors. The number of connectors may change over time as Microsoft continues to encourage other vendors to partner and create new connectors. At the time this chapter was written, the following external connectors were available:
Amazon Web Services (AWS)
Barracuda
Check Point
Palo Alto Networks
Fortinet
F5
Symantec ICDX
If an external solution is not on the data connector list, but your appliance supports saving logs as Syslog Common Event Format (CEF), the integration with Azure Sentinel is available via CEF Connector. If CEF support is not available on your appliance, but it supports calls to a REST API, you can use the HTTP Data Collector API to send log data to the workspace on which Azure Sentinel is enabled. Data ingestion from some of these connectors requires a license, while some others are free. To see an updated pricing list for the connectors, visit http://aka.ms/asbook/dataconnectors.
Ingesting data from Microsoft solutions
One way to quickly start validating Azure Sentinel’s data ingestion is to start the configuration by using Microsoft built-in connectors. To visualize data from the subscription-level events that have occurred in Azure—which includes data ranging from Azure Resource Manager (ARM) operational data to updates on service health events—you can start with Azure Activity Log. Follow the steps below to connect with Azure Activity Log:
Open Azure Portal and sign in with a user who has contributor privileges for the workspace on which Azure Sentinel will be enabled and the resource group.
Under the All services option, type Sentinel and click Azure Sentinel when it appears at the lower right, as shown in Figure 2-8.
FIGURE 2-8 Accessing Azure Sentinel in Azure Portal
Click in the workspace that was created in the “Enabling Azure Sentinel” section, earlier in this chapter.
When the Azure Sentinel dashboard opens, click Data Connectors under Configuration in the left navigation pane.
From the list of connectors, click AzureActivity; the AzureActivity page will appear, as shown in Figure 2-9.
FIGURE 2-9 Azure Activity Log connector blade
Click the Open Connector Page button, and you will see the Instructions tab, as shown in Figure 2-10.
FIGURE 2-10 Instructions tab with more details about prerequisites and configuration
Click the Configure Azure Activity logs option, and the Azure Activity Log page appears. Click the subscription to which you want to connect and click the Connect button.
Wait until you see a notification indicating the subscription was successfully connected and click the Refresh button. Ensure that the status has changed to Connected and close each blade until you see the main Data Connectors page.
Click Overview under General in the left navigation pane.
On the Overview page, you will see that there is no activity yet; this is expected because you just initiated the ingestion of Azure Activity Logs. Now you will generate some activity, and at the end of this chapter, you will check how the data flowed to Azure Sentinel. Create a new Virtual Machine with the following specifications:
Operating System: Windows Server 2016.
Resource Group: Use the same resource group that you created for the workspace in the “Enabling Azure Sentinel” section, earlier in this chapter.
Remote Desktop Connection: Enabled.
Connecting to Azure Security Center
If you have Azure Security Center enabled in your subscription, you can start ingesting the Security Alerts generated by Security Center, which provides a rich set of threat detections. Security Center will generate alerts according to the different resource types:
Infrastructure as a Service (IaaS), Virtual Machines (VMs), and non-Azure servers
Native compute
Data services
You need the Azure Security Center standard tier in order to connect with Azure Sentinel. Follow the steps below to connect to Security Center and start streaming security alerts to Azure Sentinel:
Open Azure Portal and sign in with a user who has contributor privileges for the workspace on which Azure Sentinel will be enabled as well as the resource group.
Under the All services option, type Sentinel, and click Azure Sentinel, as shown in Figure 2-11.
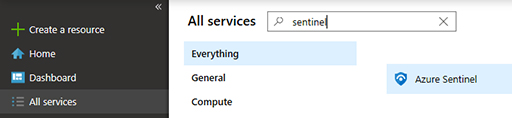
FIGURE 2-11 Accessing Azure Sentinel in Azure Portal
Click in the workspace that was created in the “Enabling Azure Sentinel” section, earlier in this chapter.
When the Azure Sentinel dashboard opens, click Data Connectors under Configuration in the left navigation pane.
Click Azure Security Center, and a new pane appears on the right side, as shown in Figure 2-12.
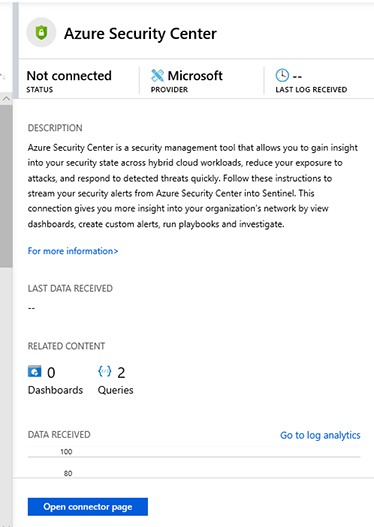
FIGURE 2-12 Azure Security Center connector
Click Open Connector Page button and the full Azure Security Center connector page appears, as shown in Figure 2-13.
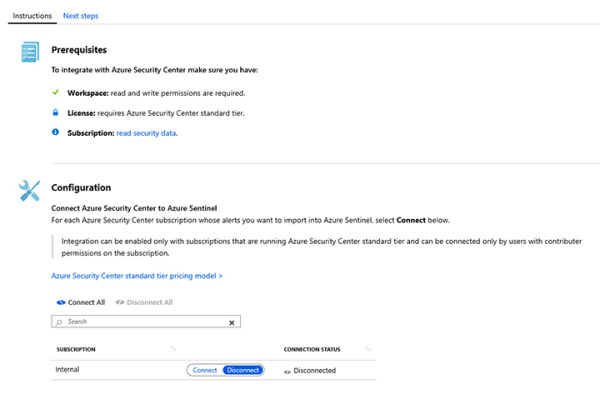
FIGURE 2-13 Azure Security Center connector page
Under the Configuration section, next to the subscription that has the Azure Security Center standard tier enabled, click Connect.
The Connection Status will temporarily appear as Connecting, and once it is finished, it will appear as Connected.
After confirming that it is connected, close the Azure Security Center page, and on the Data Connectors page, click Refresh; you will see that the Azure Security Center connector status appears as Connected, as shown in Figure 2-14.

FIGURE 2-14 Azure Security Center connector fully connected
Click the Overview option in the left pane to return to the main dashboard.
Connecting to Azure Active Directory
Azure Active Directory (Azure AD) is the identity and access-management service in the cloud. Each Azure tenant has a dedicated and trusted Azure AD directory. The Azure AD directory includes the tenant's users, groups, and apps, and it is used to perform identity and access-management functions for tenant resources. If you want to export sign-in data from Active Directory to Azure Sentinel, you must have an Azure AD P1 or P2 license.
To connect Azure Sentinel with Azure AD, follow these steps:
Open Azure Portal and sign in with a user who has global administrator or security administrator permissions. You also need to have read permission to access Azure AD diagnostic logs if you want to see connection status.
Choose the All services option, type Sentinel in the search box, and click Azure Sentinel, as shown in Figure 2-15.
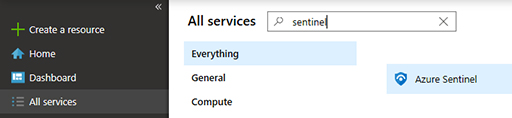
FIGURE 2-15 Accessing Azure Sentinel in Azure Portal
Click the workspace that was created in the “Enabling Azure Sentinel” section, earlier in this chapter.
When the Azure Sentinel dashboard opens, click Data Connectors under Configuration in the left navigation pane.
Click Azure Active Directory, and a new pane appears on the right side, as shown in Figure 2-16.
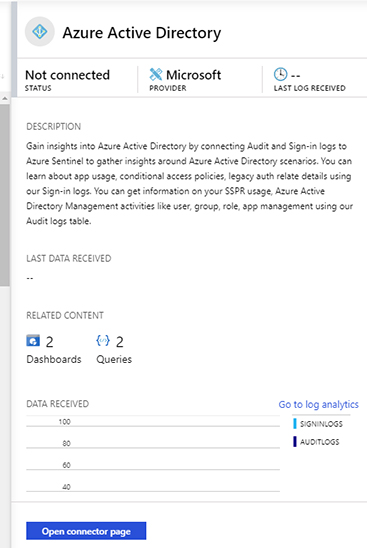
FIGURE 2-16 Azure Active Directory connector
Click Open Connector Page button, and the full Azure Active Directory connector page appears, as shown in Figure 2-17.
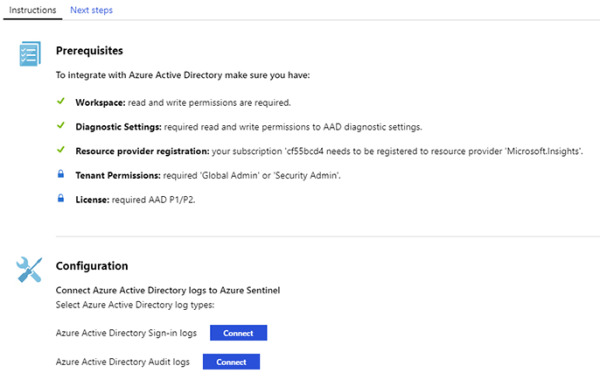
FIGURE 2-17 Azure Active Directory connector page
In the Configuration section, you have the option to connect to Azure AD sign-in logs and audit logs. Ideally, you should connect with both because it provides a broader visibility of your identity related activities. For this example, click both Connect buttons.
Once you finish connecting, both buttons will change to Disconnect.
Close this page and click the Overview option in the left pane to return to the main dashboard.
Connecting to Azure Active Directory Identity Protection
Azure Active Directory Identity Protection helps to protect your organization's identities by enabling you to configure risk-based policies that automatically respond to detected issues when a specified risk level has been reached. To perform the integration of Azure Active Directory Identity Protection with Azure Sentinel, you must have an Azure Active Directory Premium P1 or P2 license.
To connect Azure Sentinel with Azure Active Directory Identity Protection, follow these steps:
Open Azure Portal and sign in with a user who has global administrator or security administrator permissions.
In the All services text box, type Sentinel, and click Azure Sentinel when it appears as the lower right, as shown in Figure 2-18.
FIGURE 2-18 Accessing Azure Sentinel in Azure Portal
Click the workspace that was created in the “Enabling Azure Sentinel” section, earlier in this chapter.
When the Azure Sentinel dashboard opens, click Data Connectors under Configuration in the left navigation pane.
Click Azure Active Directory Identity Protection, and a new pane appears on the right side, as shown in Figure 2-19.
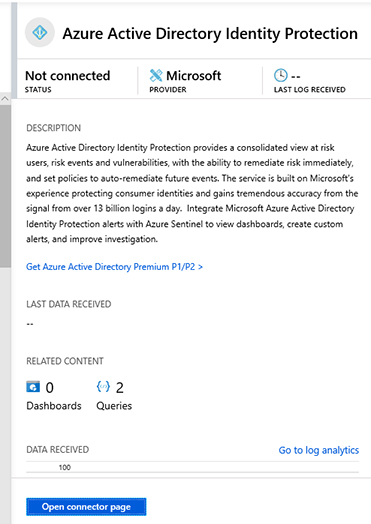
FIGURE 2-19 Azure Active Directory Identity Protection connector
Click the Open Connector Page button and the full Azure Active Directory Identity Protection connector page appears, as shown in Figure 2-20.
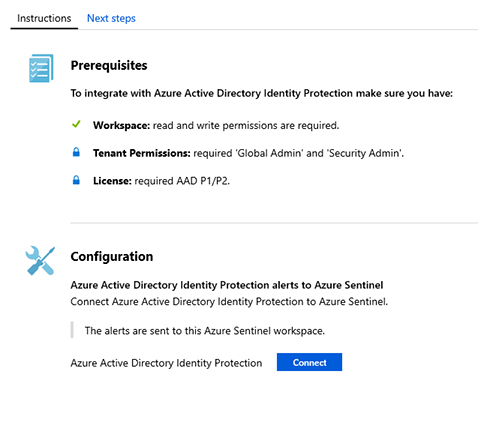
FIGURE 2-20 Azure Active Directory Identity Protection connector
Under Configuration, click the Connect button.
Once you finish connecting, the button will change to Disconnect.
Close this page and click the Overview option in the left pane to return to the main dashboard.
There are many more connectors for other Microsoft Solutions, and most of them follow the same flow as the solutions explained so far. The only thing you need to be aware of are the prerequisites for each solution. Make sure to visit the product’s webpage to better understand what permissions are necessary to connect to the target data set. In Chapter 9, “Integrating with partners,” you will learn how to connect with some partners’ solutions.
