Administering Windows Server 2012 R2: Monitoring and Auditing
- By Orin Thomas
- 6/2/2014
- Before you begin
- Lesson 1: Monitoring servers
- Lesson 2: Advanced audit policies
- Practice exercises
- Suggested practice exercises
- Answers
Lesson 2: Advanced audit policies
Auditing enables you to track both actual and attempted access and changes to objects and policies. Auditing enables you to verify that the policies that you’ve put in place to secure your organization’s network infrastructure are actually being enforced, from tracking modifications to sensitive user accounts through to access to sensitive files and folders. In this lesson, you will learn about advanced audit policy, how to configure expression-based audit policies, and how you can use auditpol.exe to manage auditing.
Configuring advanced auditing

There are two sets of audit policies in a Group Policy Object (GPO): traditional audit policies and advanced audit policies. The traditional audit policies are located in the Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Audit Policies node and are shown in Figure 10-22. They are the audit policies that have been available with the Windows Server operating system since Windows 2000. The drawback of these policies is that they are general, and you can’t be specific in the way you configure auditing. When you use these policies, you’ll not only audit the events that you’re interested in but you’ll also end up auditing many events that you don’t need to know about.
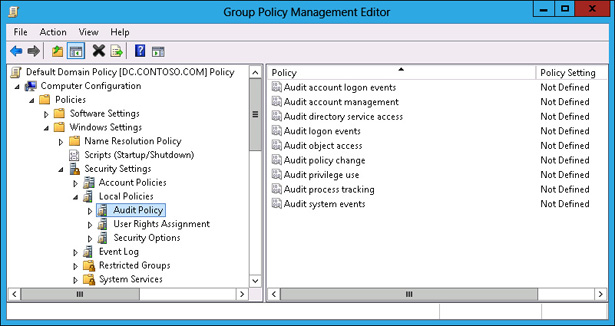
FIGURE 10-22 General auditing policies
The advanced audit policies enable you to be more specific in the types of activity you audit. The advanced audit policies are located under the Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration node, as shown in Figure 10-23.
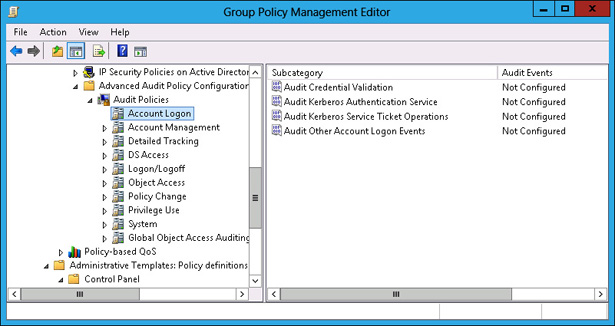
FIGURE 10-23 Advanced audit policies
There are 10 groups of audit policy settings and 58 individual audit policies available through Advanced Audit Policy Configuration. The audit policy groups contain the following settings:
- Account Logon You can audit credential validation and Kerberos-specific operations.
- Account Management You can audit account management operations, such as changes to computer accounts, user accounts, and group accounts.
- Detailed Tracking You can audit encryption events, process creation, process termination, and RPC events.
- DS Access You can audit Active Directory access and functionality.
- Logon/Logoff You can audit logon, logoff, and other account activity events, including IPsec and Network Policy Server (NPS) events.
- Object Access You can audit access to objects including files, folders, applications, and the registry.
- Policy Change You can audit changes to audit policy.
- Privilege Use You can audit the use of privileges.
- System You can audit changes to the security subsystem.
- Global Object Access Auditing You can configure expression-based audit policies for files and the registry.
Implementing expression-based audit policies
Traditional object audit policies involve specifying a group and configuring the type of activities that will trigger an event to be written to the security log. Specifying that an audit event will be written each time a member of the Managers group accesses a file in a specific folder is a good example.

Expression-based audit policies enable you to go further. These policies enable you to put conditions as to when auditing might occur. For example, you might want to configure auditing so that members of the Managers group have access to sensitive files tracked only when they access files from computers that aren’t part of the Managers_Computers group. Figure 10-24 shows auditing configured in this way. This way, you don’t bother tracking access when members of this group access sensitive files from within the office, but you do track all access to those sensitive files when members of this group are accessing them from an unusual location.
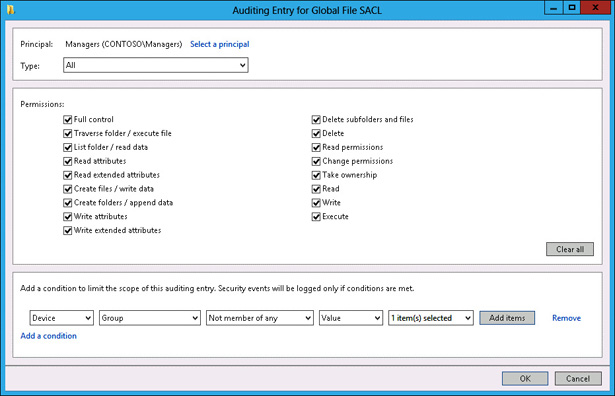
FIGURE 10-24 Expression-based audit policies
You can integrate expression-based audit policies with Dynamic Access Control (DAC) to create targeted audit policies that are based on user, computer, and resource claims. Instead of just adding claims based on user or device group membership, the claim can be based on document metadata such as confidentiality settings and site location. You can configure expression-based audit policies at the file or folder level, or apply them through Group Policy using policies in the Global Object Access Auditing node of Advanced Audit Policy Configuration.
Configuring file and folder auditing
After you configure auditing of object access, either through the traditional or advanced audit policies, you can configure auditing at the file and folder level. The simplest way to configure auditing is at the folder level because you can then configure all folders and subfolders to inherit those auditing settings. If you change the auditing settings at the folder level, you can use the Replace All Child Object Auditing Entries option to apply the new auditing settings to the folder’s child files and folders.
You can configure auditing for a specific file and folder through the Advanced button on the Security tab of the object’s properties. You can configure basic success and failure auditing, as shown in Figure 10-25. You can also configure expression-based auditing so that activity by members of a specific security group are audited only if other conditions, such as membership of other security groups, are also met.
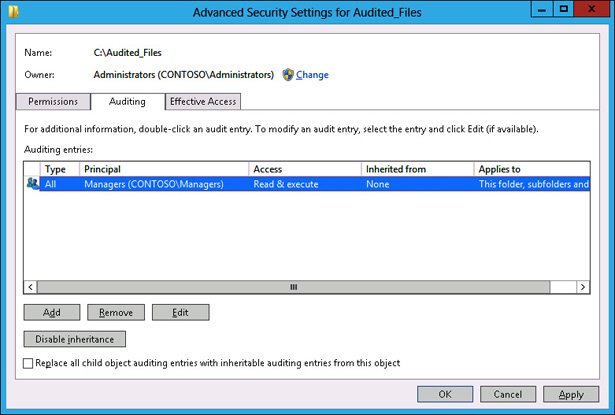
FIGURE 10-25 Configuring basic success and failure auditing
The advantage of using Global Object Access Auditing is that when you have it configured, you can use file classification to apply metadata to files and then automatically have auditing enabled for those files. For example, using file classification and DAC, you can configure a Windows Server 2012 R2 file server so that all files that contain the phrase “code secret” are marked as Sensitive. You can then configure Global Object Access Auditing so that all access to files marked as Sensitive are automatically audited. Instead of having an administrator track down all the files that are sensitive and configuring auditing on those files, the process is automatic. All that needs to happen to trigger it is the inclusion of the phrase “code secret” in the file.
Using auditpol with auditing

Auditpol.exe is a command-line utility that you can use to configure and manage audit policy settings from an elevated command prompt. You can use auditpol.exe to perform the following tasks:
- View the current audit policy settings with the /Get subcommand
- Set audit policy settings with the /Set subcommand
- Display selectable policy elements with the /List subcommand
- Back up and restore audit policies using the /Backup and /Restore subcommands
- Delete all per-user audit policy settings and reset the system policy settings using the /Clear subcommand
- Remove all per-user audit policy settings and disable all system policy settings using the /Remove subcommand
For example, to enable success and failure auditing for the File System subcategory of Object Access, execute this command.
Auditpol.exe /set /subcategory:"File System" /success:Enable /failure:Enable
To view the current audit policy settings for all audit policies, issue this command.
Auditpol.exe /get /category:*
To view the current audit policy settings for a specific category, such as Object Access, issue this command.
Auditpol.exe /get /category:"Object Access"
Lesson summary
- Advanced audit policies enable you to perform more granular auditing than is possible with the traditional auditing policies available in earlier versions of Windows server.
- Expression-based audit policies enable you to configure auditing based on object metadata. You can also use expression-based audit policies to perform conditional auditing.
- After you have enabled the auditing of object access, you can configure auditing at the file and folder level. File-level and folder-level auditing supports expression-based audit policies.
- You can use the auditpol.exe command-line utility from an elevated command prompt to configure and manage audit policy settings.
Lesson review
Answer the following questions to test your knowledge of the information in this lesson. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
Which of the following commands should you use to enable success and failure auditing for all audit policies under the Object Access category on a computer running Windows Server 2012 R2?
- Auditpol.exe /set /subcategory:"File System" /success:Enable /failure:Enable
- Auditpol.exe /set /Category:"Object Access" /success:Enable /Failure:Enable
- Auditpol.exe /get /Category:"Object Access" /success:Disable /Failure:Disable
- Auditpol.exe /get /Category:"Object Access" /success:Disable /Failure:Enable
You want to enable failure auditing, but not success auditing, for all audit policies under the Object Access category on a computer running Windows Server 2012 R2. Which of the following commands should you use to accomplish this goal?
- Auditpol.exe /get /Category:"Object Access" /success:Disable /Failure:Enable
- Auditpol.exe /get /Category:"Object Access" /success:Disable /Failure:Disable
- Auditpol.exe /set /Category:"Object Access" /success:Enable /Failure:Enable
- Auditpol.exe /set /subcategory:"File System" /success:Enable /failure:Enable
You want to enable success and failure auditing only for the File System subcategory. Which of the following commands should you use to accomplish this goal?
- Auditpol.exe /set /Category:"Object Access" /success:Enable /Failure:Enable
- Auditpol.exe /get /Category:"Object Access" /success:Disable /Failure:Enable
- Auditpol.exe /set /subcategory:"File System" /success:Enable /failure:Enable
- Auditpol.exe /get /Category:"Object Access" /success:Disable /Failure:Disable
You want to disable all success and failure auditing on all auditing subcategories under the Object Access category. Which of the following commands should you use to accomplish this goal?
- Auditpol.exe /get /Category:"Object Access" /success:Disable /Failure:Disable
- Auditpol.exe /get /Category:"Object Access" /success:Disable /Failure:Enable
- Auditpol.exe /set /Category:"Object Access" /success:Enable /Failure:Enable
- Auditpol.exe /set /subcategory:"File System" /success:Enable /failure:Enable

 Quick check
Quick check