Managing Group Policy Application and Infrastructure in Windows Server 2012 R2
- By Orin Thomas
- 6/2/2014
- Before you begin
- Lesson 1: Maintaining Group Policy Object
- Lesson 2: Managing Group Policy application
- Practice exercises
- Suggested practice exercises
- Answers
Lesson 2: Managing Group Policy application
For environments in which you need to apply more than one Group Policy, understanding the rules of precedence is critical. Not only do you need to understand that where you apply a Group Policy determines its overall influence but also that GPOs may or may not apply due to inheritance blocks, security filtering, or loopback processing. In this lesson, you’ll learn the rules on Group Policy application and how to determine which Group Policy settings have precedence in complex environments.
Policy processing precedence

In organizations with large Group Policy deployments, multiple GPOs might apply to a single user account or computer account; or when a user is signed on to a specific computer, to both. Group Policy processing precedence is the set of rules that determines which Group Policy items apply when multiple GPOs are configured.
Group Policies are processed in the following manner:
- Local Settings configured at the local level apply first. If multiple local policies apply, settings in machine policies apply first, settings in admin and nonadmin local policies override them, and settings in per-user policies override any configured at the machine and admin/nonadmin level.
Site Policies based on location apply next. Any settings configured at the site level override settings configured at the local level. You can link multiple GPOs at the site level. When you do this, policies with a lower numerical link order override policies with a higher numerical link order. For example in Figure 5-12, settings in the Melbourne-Computer policy override settings configured in the Melbourne-User policy.
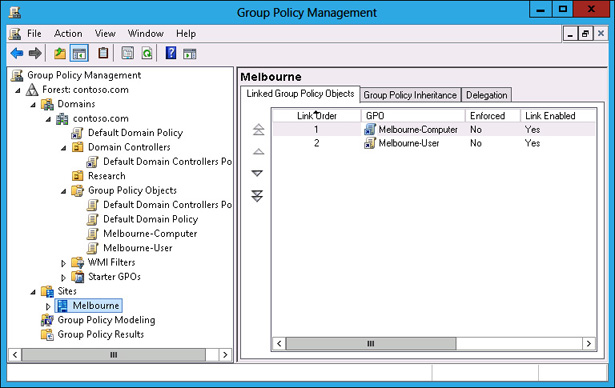
FIGURE 5-12 GPO link order
- Domain Settings applied at the domain level override settings applied at the site and local levels. You can link multiple GPOs at the domain level. The Default Domain Policy is linked at this level.
- Organizational unit (OU) Settings applied at the organizational unit level override settings applied at the domain, site, and local levels. When an account is a member of a child OU, policies applied at the child OU level override policies applied at the parent OU level. You can apply multiple GPOs at the OU level. Policies with a lower numerical link order override policies with a higher numerical link order.
Group Policy processing precedence is relevant only when there are conflicts in policies. If policy A applies at the domain level, and policy B applies at the OU level, both policy A and policy B apply.
Policy enforcement and blocking
When configuring a Group Policy, you can choose to enforce that policy. To enforce a Group Policy, right-click that policy at the location in which you link the policy and then click Enforced. When you choose to enforce a policy, that policy will apply and override settings configured at other levels. For example, normally a policy linked at the OU level would override a policy linked at the domain level. If you configure the policy at the domain level as Enforced, it instead overrides the policy linked at the OU level.

The Block Inheritance function enables you to block policies applied at earlier levels. For example, you can use Block Inheritance at the OU level to block policies applied at the domain and site level. Block Inheritance does not stop the application of policies configured as Enforced. For example, Figure 5-13 shows the Research OU configured with the Block Inheritance setting. The Melbourne-Computer policy, applied at the domain level as Enforced, still applies because a setting of Enforced overrides a setting of Block Inheritance.
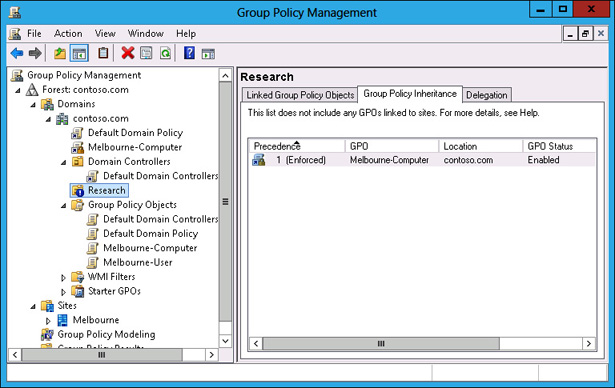
FIGURE 5-13 Override versus Enforced
Group Policy security filtering

Security filtering enables you to configure permissions on GPOs. By default, Group Policies apply to the Authenticated Users group. By changing the default permissions, you can make the Group Policy apply only to a specific group. For example, if you remove the Authenticated Users group and add another security group such as the Melbourne-Users group (shown in Figure 5-14), the Group Policy applies to only that configured security group.
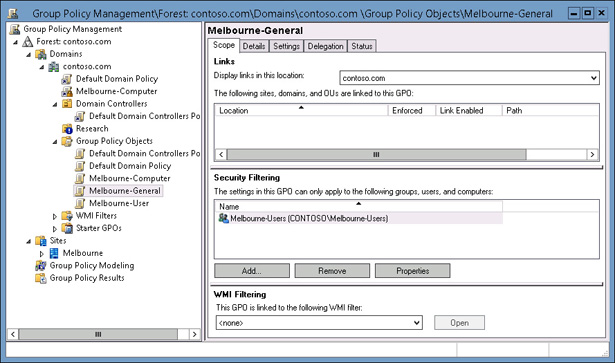
FIGURE 5-14 Security filtering
When considering whether to use security filtering, keep the following in mind:
- A security filter applies to the GPO, so it applies wherever the GPO is linked. You can’t have one security filter apply to the GPO when linked at the domain level, and another security filter apply to the GPO when linked at the OU level.
- Filtered policies still need to be checked during the Group Policy processing process, which can increase the amount of time spent on Group Policy processing. Startup and logon times may increase.
It is also possible to apply a Deny permission on the basis of security account or group. Deny permissions override Allow permissions. You block a particular security group from receiving a Group Policy by setting the Apply Group Policy (Deny) advanced permission, as shown for the Sydney-Users group for the Melbourne-General GPO in Figure 5-15. You can do this on the Delegation tab of a GPO’s properties instead of the Scope tab.
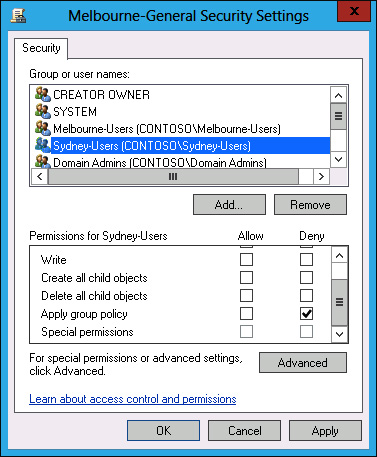
FIGURE 5-15 Security filtering
Group Policy WMI filtering
WMI filtering enables you to filter the application of policy based on the results of a WMI query. For example, you might write a WMI query to determine whether a computer has an x86 or x64 processor, or whether there is more than a certain amount of disk space available. WMI queries are often used with policies related to software deployment to determine whether the target computer has the appropriate system resources to support the installation of the application.
The drawback of WMI queries is that they are complicated for systems administrators who are unfamiliar with programming beyond simple scripting. WMI queries also cause significant delays in Group Policy processing. In environments in which sophisticated logic needs to be applied to targeted application distribution, products such as Microsoft System Center 2012 Configuration Manager are more appropriate. System Center 2012 Configuration Manager enables administrators performing software deployment to configure ways of checking hardware configuration prior to software deployment that do not require writing queries in WMI Query Language (WQL).
You can create WMI filters by using the New WMI Filter dialog box (shown in Figure 5-16).
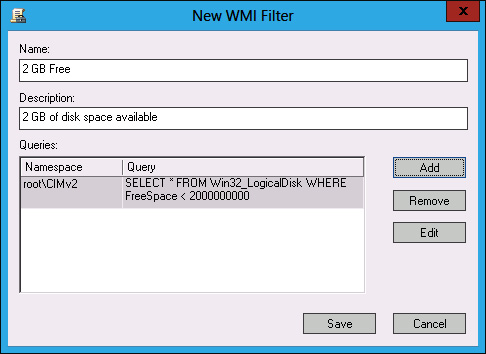
FIGURE 5-16 Creating a WMI filter
Loopback processing
As you are aware, each GPO has two distinct sections: Computer Configuration and User Configuration (see Figure 5-17). The resultant policies for a user are based on the cumulative user configuration settings in GPOs that apply to the user’s accounts at the site, domain, and OU setting. The resultant computer policies are applied based on the cumulative computer configuration settings in GPOs that apply to the computer’s account at the site, domain, and OU level.
FIGURE 5-17 GPO structure

In some situations, you’ll want only the GPOs that apply to the computer account to apply. You might want to do this with conference room computers, for which you want people to be able to sign on with domain accounts but to have a very controlled configuration. When you enable loopback processing, user settings are determined based on the settings in the User Configuration settings area of GPOs that apply to the computer account.
There are two types of loopback processing that you can configure by setting the Group Policy loopback processing mode policy, shown in Figure 5-18, and located under Computer Configuration\Administrative Templates\System\Group Policy: Replace And Merge.
- Replace When you configure Replace, only the GPOs that apply to the computer account will apply. Settings in the User Configuration area of the GPOs that apply to the computer account will apply.
Merge The settings in the User Configuration area of GPOs that apply to the user account will still apply, but will be overridden by settings in the User Configuration area of GPOs that apply to the computer account.
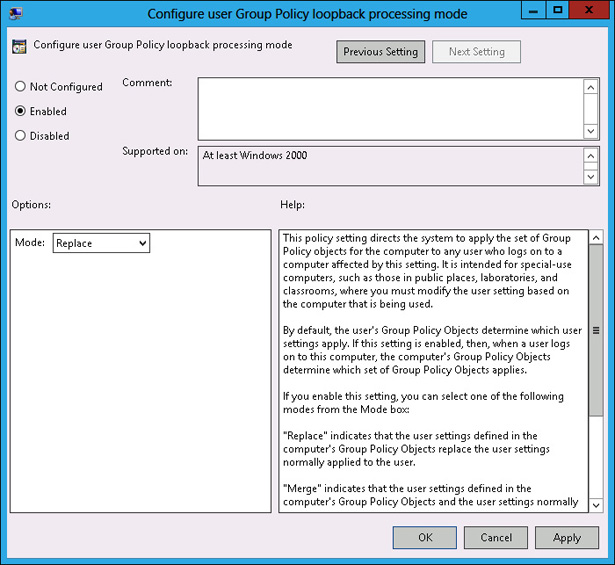
FIGURE 5-18 Loopback processing policy

Slow-link processing enables you to configure Group Policy application to be performed in a different manner, depending on the speed of the connection from the client to the domain controller. It enables you to block activities such as software deployment when the connection between Active Directory and the client is detected as falling below a particular threshold. You configure slow link detection by configuring the Group Policy slow link detection policy, as shown in Figure 5-19. This policy is located under Computer Configuration\Administrative Templates\System\Group Policy. When a slow link is detected, registry settings from administrative templates, security policies, EFS recovery policy, and IPsec policies are applied. Policies related to application deployment, scripts, folder redirection, and disk quotas will not be applied.
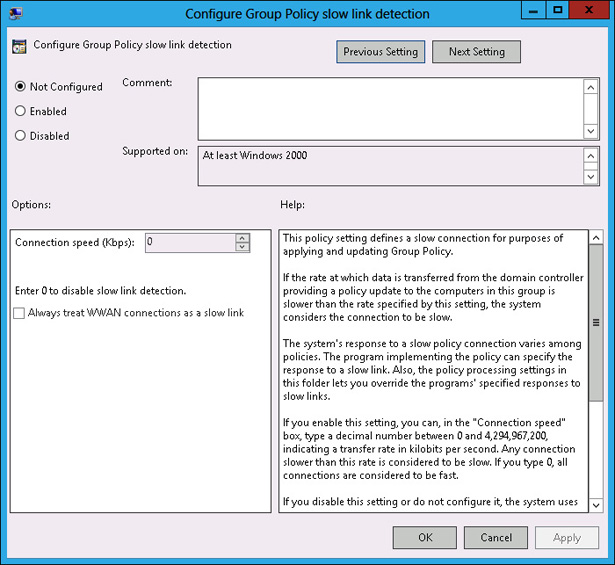
FIGURE 5-19 Slow link detection
Group Policy caching
Group Policy caching reduces the amount of time taken to process Group Policy during computer startup and user sign on. Rather than retrieve the Group Policies that apply to the computer from a domain controller when a computer starts up or a user signs on, the client will use a cached copy of the last Group Policies downloaded from the domain controller. After this initial application of the cached policies during startup and user sign on, policies will be retrieved and applied normally from a domain controller. You enable Group Policy caching by configuring the Configure Group Policy Caching policy as shown in Figure 5-20. This policy is located under Computer Configuration\Policies\Administrative Templates\System\Group Policy. Group Policy caching applies only to computers running Windows Server 2012 R2, Windows 8.1, or Windows RT 8.1.
FIGURE 5-20 Configure Group Policy caching
Force Group Policy update
Windows Server 2012 and later support remote Group Policy update. Remote Group Policy update allows you to force a remote computer to perform a Group Policy update without having to sign on to the computer and run the GPUpdate.exe command. Remote Group Policy update will work on clients running the Windows Vista and later operating system. Remote Group Policy requires the following firewall rules be enabled on clients:
- Remote Scheduled Tasks Management (RPC)
- Remote Scheduled Tasks Management (RPC-EPMAP)
- Windows Management Instrumentation (WMI-In)
You can run remote Group Policy update from the Group Policy Management Console by right-clicking on a container or OU. An update will run on all computers within the container or OU as well as on any computer accounts stored within child OUs. Figure 5-21 shows the result of running remote Group Policy update on the Domain Controllers container. You can also use the Invoke-GPUpdate Windows PowerShell cmdlet to trigger a remote Group Policy update. The advantage of the Windows PowerShell cmdlet is that you can target a specific computer rather than all computer accounts in an OU.
FIGURE 5-21 Remote Group Policy update
Lesson summary
- Group Policies are processed in the following order: local, site, domain, and OU. Policies processed later override policies processed earlier.
- When there are parent and child OUs, and the user or computer account is a member of the child OU, the policy applied at the child OU overrides policies applied at the parent OU.
- Policy processing order is important only when policies conflict.
- A policy with the Override setting will override other policies in the processing order, including when Block Inheritance has been configured.
- Security filtering applies on a GPO, no matter where it is linked.
- Loopback processing enables GPO settings applied to the computer account to override GPO settings applied to the user account.
- Slow-link processing enables you to configure policies not to be processed when low bandwidth connections to Active Directory are detected.
- Group Policy caching allows cached copies of GPOs that apply to users and computers to be applied at startup and sign on.
- Remote Group Policy update allows you to force a Group Policy update on a remote client. Remote Group Policy update requires that 3 firewall rules be configured on clients.
Lesson review
Answer the following questions to test your knowledge of the information in this lesson. You can find the answers to these questions and explanations of why each answer choice is correct or incorrect in the “Answers” section at the end of this chapter.
You want to ensure that a Group Policy applies only to computers that have more than 2 gigabytes (GB) of disk space. Which of the following should you configure to accomplish this goal?
- Security filtering
- WMI filtering
- Loopback processing
- Slow-link processing
A Group Policy named Alpha applies at the site level. A Group Policy named Beta is assigned link order 2 at the domain level. A Group Policy named Gamma is assigned link order 1 at the domain level. A Group Policy named Delta is assigned to the Research OU. A computer account is located in the Research OU. If the same setting is configured differently in the Alpha, Beta, Gamma, and Delta GPOs, which GPO’s version of this setting will apply to the computer?
- Alpha
- Beta
- Gamma
- Delta
A Group Policy named Alpha applies at the site level. A Group Policy named Beta is assigned link order 2 at the domain level. A Group Policy named Gamma is assigned link order 1 at the domain level. A Group Policy named Delta is assigned to the Research OU. A computer account is located in the Research OU. GPO Gamma is configured with the No Override setting. If the same setting is configured differently in the Alpha, Beta, Gamma, and Delta GPOs, which GPO’s version of this setting will apply to the computer?
- Alpha
- Beta
- Gamma
- Delta
A Group Policy named Alpha applies at the site level. A Group Policy named Beta is assigned link order 2 at the domain level. A Group Policy named Gamma is assigned link order 1 at the domain level. A Group Policy named Delta is assigned to the Research OU. A computer account is located in the Research OU. GPO Beta is configured with the No Override setting. OU Research is configured with the Block Inheritance setting. If the same setting is configured differently in GPOs Alpha, Beta, Gamma, and Delta, which GPO’s version of this setting will apply to the computer?
- Alpha
- Beta
- Gamma
- Delta
You have a policy applied at the domain level that you don’t want applied to five computers in your organization. Which of the following should you configure to accomplish this goal?
- Security filtering
- WMI filtering
- Loopback processing
- Slow-link processing

 Quick check
Quick check