Manage policies and profiles
- By Andrew Bettany and Andrew Warren
- 11/29/2021
- Skill 2.1: Implement compliance policies for devices
- Skill 2.2: Configure device profiles
In this sample chapter from Exam Ref MD-101 Managing Modern Desktops, 2nd Edition, you will learn how to use traditional user profile management and how Azure Active Directory enables users to roam their Windows settings from any device, even when working remotely.
The MD-101: Managing Modern Desktops exam focuses on how you will manage Windows 10 devices using modern management tools and services, such as Microsoft Endpoint Manager and Microsoft Intune. Because of the recent move toward cloud-based device management, many organizations may currently rely on traditional technologies including Group Policy and Configuration Manager for their device management requirements. Microsoft supports both environments and encourages larger organizations to co-manage their infrastructure using both traditional and modern cloud-based solutions.
You need to understand how to implement and configure devices using both policies and profiles in Microsoft Intune. In this chapter, you will learn how to use traditional user profile management and how Azure Active Directory enables users to roam their Windows settings from any device, even when working remotely.
Skills covered in this chapter:
Skill 2.1: Implement compliance policies for devices
Skill 2.2: Configure device profiles
Skill 2.3: Manage user profiles
Skill 2.1: Implement compliance policies for devices
Once you begin to manage Windows 10 devices using standalone Microsoft Intune or integrated into Microsoft Endpoint Manager, you will want to implement conditional access to provide granular access control for your corporate resources. These resources can include data contained in controlled applications. Intune works together with Azure Active Directory (Azure AD) to actively check the status of enrolled devices against your policies each time a resource such as corporate email is accessed.
With Microsoft Intune, you can stipulate the necessary compliance checks that Azure AD will perform on enrolled devices. By deploying compliance policies, devices can be allowed or denied access to your corporate resources. You need to understand how to plan, implement, and manage these policies to meet organizational security requirements.
Plan device compliance policies
Many organizations are regulated and must comply with laws and regulations, such as those shown in Table 2-1. To remain in compliance, administrators need to configure and manage devices and any data contained on them, in accordance with the corporate security and compliance requirements. Modern management enables administrators to control devices and restrict their usage when accessing corporate data.
TABLE 2-1 Regulations and compliance
Regulation |
Region |
Requirement |
|---|---|---|
HIPAA (Health Insurance Portability and Accountability Act of 1996) |
USA |
User isn’t prompted to Multifactor Authentication (MFA). |
Sarbanes-Oxley Act |
USA |
The Chief Financial Officer (CFO) and Chief Executive Officer (CEO) have joint responsibility for the financial data. Administrators will need to keep financial data secure and free from tampering, theft, and deletion. |
Gramm-Leach-Bliley Act |
USA |
Responsibility for security lies within the entire board of directors. IT administrators, while not legally bound, will be delegated the implementation and management of IT security. |
GDPR (General Data Protection Regulation) |
EU |
Requires all enterprises regardless of their location to adhere to EU privacy laws relating to any individual living in the EU. |
Using Microsoft Intune, you can define compliance policies. Once compliance policies have been created, they can be assigned to enrolled devices and device groups. Devices will be configured using the compliance policy and become compliant.
Each time that a device attempts to access corporate resources, such as a SharePoint TeamSite or corporate email client, the policy on the device will be evaluated and its compliance status determined. Only compliant devices will be granted access to the resources.
Organizations must have Azure AD Premium P1 or P2 licenses, and each device requires an Intune license to use compliance policies.
The following device platforms can be managed using compliance policies once they have been enrolled into Intune:
Android and Android Enterprise
iOS and macOS
Windows 10 and Windows 8.1
When considering how your organization will achieve compliance, you may need to review the features available and support for compliance policies. Each compliance policy within Intune is platform specific, and the actual compliance policy settings available will vary depending on the settings that are exposed to the mobile device management (MDM) framework by the platform vendor. For example, BitLocker encryption is available only on Windows devices and Google Play Protect is available only on the Android platform.
Require A Password To Access Devices For example, a PIN or password.
Local Data Encryption BitLocker encryption or other boot protection such as Secure Boot.
Is The Device Jailbroken Or Rooted Often, a device that has been jailbroken or rooted will be more vulnerable to malware attack.
Minimum Operating System Version Required Prevents outdated software being used, which may be more vulnerable to malware attack.
Maximum Operating System Version Allowed Prevents software that has not been tested or approved for corporate use from being used.
Protected Against Malware Threats Requires the device to have an antimalware solution enabled, signatures up to date, or real-time protection enabled.
Network Location-Based Blocks access to a corporate network if a device leaves a defined location.
Noncompliant devices
An unenrolled device that attempts to access corporate resources will be deemed to be noncompliant and access will be blocked. If a user subsequently enrolls the device in Intune and re-attempts to access corporate resources, the Intune compliance policies will be evaluated again, and the device may or may not be granted access based on the current policies in place.
The outcome for noncompliant, but enrolled, devices will typically be to block access to company resources. However, you can configure actions for noncompliance as follows:
Send Email To End User You can customize an email notification that is sent to the end user. You can customize the recipients, subject, and message body. Also, you can add a company logo and contact information. Lastly, you can add any instructions on how the user can bring the device into a compliant state.
Remotely Lock The Noncompliant Device Devices that are noncompliant can be remotely locked. The user will need to enter a PIN or password to unlock the device.
Mark Device Noncompliant The noncompliant device can be allowed access to company resources as long as the device is made compliant within a specified grace period. After the grace period has expired, noncompliant devices will be blocked. Alternatively, the grace period can be set to zero, and the action will take effect immediately.
To configure a notification email message template, follow these steps:
Sign into the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com as a global administrator.
Select Devices, and then under Policy, click Compliance policies.
On the Compliance policies page, select Notifications.
Select Create notification.
On the Create notification blade, as shown in Figure 2-1, enter the name of the notification.
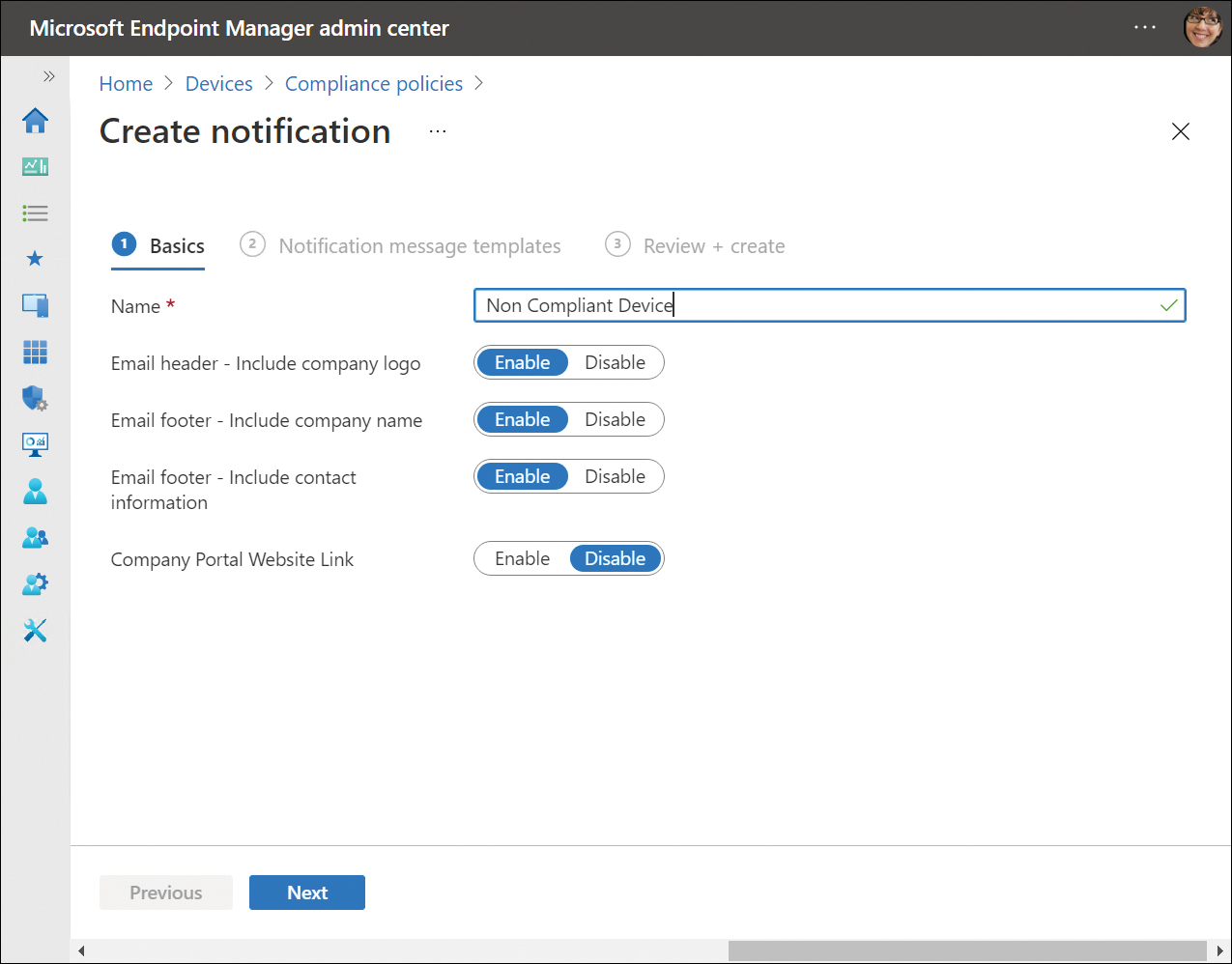
Figure 2-1 Configure notification email
On the Email header–include company logo, select Enable or Disable.
On the Email footer–include company name, select Enable or Disable.
On the Email footer–include contact information, select Enable or Disable.
On the Company Portal Website Link, select Enable or Disable.
Click Next.
On the Notification message template page, select the Locale.
For the subject, enter a message subject.
In the message box, enter your notification message.
If this is your only message template, under Is Default, select the check box to make this message template the default template.
Click Next.
On the Review + Create page, review the details and then click Next.
The notification is created and listed in the list of notifications.
Network location-based compliance policy
Managing devices is easy when they are confined within a traditional office setting. Administrators often find that once mobile devices are permanently away from the office and require access to corporate resources, the challenge of managing them can become more difficult.
Within the office, devices are provided with network access, such as wired Ethernet and secured Wi-Fi connections. Access to corporate resources via office-based devices is strictly controlled and monitored, with all user activity to cloud apps and web traffic subject to firewall constraints and corporate security and compliance scrutiny.
Using MDM, administrators can block access to a corporate network, app, or resource even when a device leaves a specific location. You must first define a location within Microsoft Endpoint Manager to provide this functionality.
To create a network location-based compliance policy (also known as network fencing), follow these steps:
Sign into the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com as a global administrator.
Select Devices, and then under Policy, click Compliance policies.
On the Compliance policies page, select Locations.
On the Locations page, select Create, as shown in Figure 2-2, and complete the following properties. Note that some properties are required, and some are optional, as noted below:
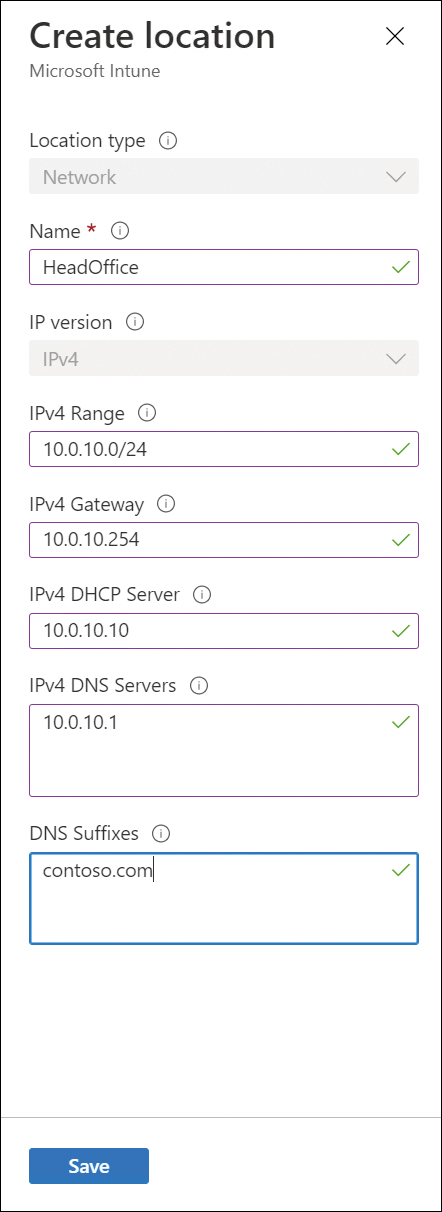
Figure 2-2 Create location
Enter a name for the location, such as HeadOffice. (Required)
Enter an IPv4 range with CIDR (Classless Interdomain Routing) notation, such as 10.0.10.0/24. If the device uses one of these IPv4 addresses, then the device will be deemed compliant. (Optional)
Enter the IPv4 Gateway address, such as 10.0.10.254. (Optional)
Enter the IPv4 DHCP Server address, such as 10.0.10.10. (Optional)
Enter a list of IPv4 DNS Server addresses, such as 10.0.10.1. If the device uses one of these IPv4 DNS Server addresses, then the device will be compliant. (Optional)
Enter a list of DNS Suffixes, such as contoso.com. If the device uses one of these DNS Suffixes, then the device will be compliant. (Optional)
Click Save.
Once you have created one or more locations, you can create a policy to ensure devices must be connected to a trusted work network to be compliant. The policy can be used with conditional access policies to provide access to corporate resources only when the device is connected to the work network as defined in the location. Whenever the device moves away from the work network, the device becomes noncompliant and loses access to corporate resources.
If you are using Android devices that use the Android device administrator platform, you can create a standalone compliance policy that requires devices to be connected to your corporate network, which is assigned to the device or device group. This is then evaluated independently, or you can use an existing compliance policy and select a pre-defined location within the policy properties.
To add a location to an existing Android device administrator platform compliance policy, follow these steps:
Sign into the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com as a global administrator.
Select Devices, and then under Policy, click Compliance policies.
On the Compliance policies blade, select an existing compliance policy that is targeting Android device administrator platform devices.
Under Manage, click Properties.
On the Properties blade, choose Locations and select Edit.
On the Locations page, choose Select locations.
From the list on the Select locations blade, choose the location and choose Select.
Click Review + Save, and then on the Policy Properties page, click Save.
Once you have added a location in a compliance policy, if the device isn’t connected to the selected locations, then it’s immediately considered noncompliant.
Implement device compliance policies
Device compliance policies can be used with or without conditional access policies and achieve the following outcomes:
With conditional access Devices in compliance can access corporate resources. Devices that are not compliant will be blocked from accessing corporate resources.
Without conditional access Effectively, these policies evaluate the compliance status of a device only. Used alone, there are no access restrictions to corporate resources because of a compliance policy.
You can use compliance policies without conditional access policies to evaluate the status of your devices. You can report information relating to device platform characteristics, such as the following:
The number of devices that do not have compliance policies
The number of devices that are not encrypted
Whether devices are jailbroken or rooted
Threat agent status
A list of the device attributes that can be reported is shown in Table 2-2.
TABLE 2-2 Device data available in Microsoft Intune
Detail |
Description |
Platform |
|---|---|---|
Name |
The name of the device. |
Windows, iOS |
Management Name |
The device name used only in the console. Changing this name won’t change the name on the device. |
Windows, iOS |
UDID |
The device’s Unique Device identifier. |
Windows, iOS |
Intune Device ID |
A GUID that uniquely identifies the device. |
Windows, iOS |
Serial Number |
The device’s serial number from the manufacturer. |
Windows, iOS |
Shared Device |
If Yes, the device is shared by more than one user. |
Windows, iOS |
User Approved Enrollment |
If Yes, the device has user approved enrollment, which lets admins manage certain security settings on the device. |
Windows, iOS |
Operating System |
The operating system used on the device. |
Windows, iOS |
Operating System Version |
The version of the operating system on the device. |
Windows, iOS |
Operating System Language |
The language set for the operating system on the device. |
Windows, iOS |
Total Storage Space |
The total storage space on the device (in gigabytes). |
Windows, iOS |
Free Storage Space |
The unused storage space on the device (in gigabytes). |
Windows, iOS |
IMEI |
The device’s International Mobile Equipment Identity. |
Windows, iOS, Android |
MEID |
The device’s Mobile Equipment IDentifier. |
Windows, iOS, Android |
Manufacturer |
The manufacturer of the device. |
Windows, iOS, Android |
Model |
The model of the device. |
Windows, iOS, Android |
Phone Number |
The phone number assigned to the device. |
Windows, iOS, Android |
Subscribe Carrier |
The device’s wireless carrier. |
Windows, iOS, Android |
Cellular Technology |
The radio system used by the device. |
Windows, iOS, Android |
WiFi MAC |
The device’s Media Access Control address. |
Windows, iOS, Android |
ICCID |
The Integrated Circuit Card Identifier, which is a SIM card’s unique identification number. |
Windows, iOS, Android |
Enrolled Date |
The date and time the device was enrolled in Intune. |
Windows, iOS, Android |
Last Contact |
The date and time the device last connected to Intune. |
Windows, iOS, Android |
Activation Lock Bypass Code |
The code that can be used to bypass the activation lock. |
Windows, iOS, Android |
Azure AD Registered |
If Yes, the device is registered with Azure Directory. |
Windows, iOS, Android |
Compliance |
The device’s compliance state. |
Windows, iOS, Android |
EAS Activated |
If Yes, the device is synchronized with an Exchange mailbox. |
Windows, iOS, Android |
EAS Activation ID |
The device’s Exchange ActiveSync identifier. |
Windows, iOS, Android |
Supervised |
If Yes, administrators have enhanced control over the device. |
Windows, iOS, Android |
Encrypted |
If Yes, the data stored on the device is encrypted. |
Windows, iOS, Android |
Create a device compliance policy
Before creating a device compliance policy, you should create a compliance notification so that Microsoft Endpoint Manager understands how to respond to both compliant and noncompliant devices. You created a compliance notification in the previous section. With the notification in place, it serves as a backstop should the device be noncompliant.
Perform these steps to create a compliance policy that requires enrolled Android devices to enter a password of a specific length before access is granted to corporate resources:
Sign into the Microsoft Endpoint Manager admin center at https://endpoint.microsoft.com as a global administrator.
Select Devices, and then under Policy, click Compliance policies.
On the Compliance policies page, click Create Policy.
On the Create a policy blade, under Platform, select Android device administrator and select Create.
On the Android compliance policy page, on the Basics tab, type the name Android Password Compliance, add a Description, and select Next.
On the Compliance settings tab, modify the settings you require and then select System Security.
On the System Security area, click Require for the Require A Password To Unlock Mobile Devices option.
Select At least numeric for the Required password type option, as shown in Figure 2-3.
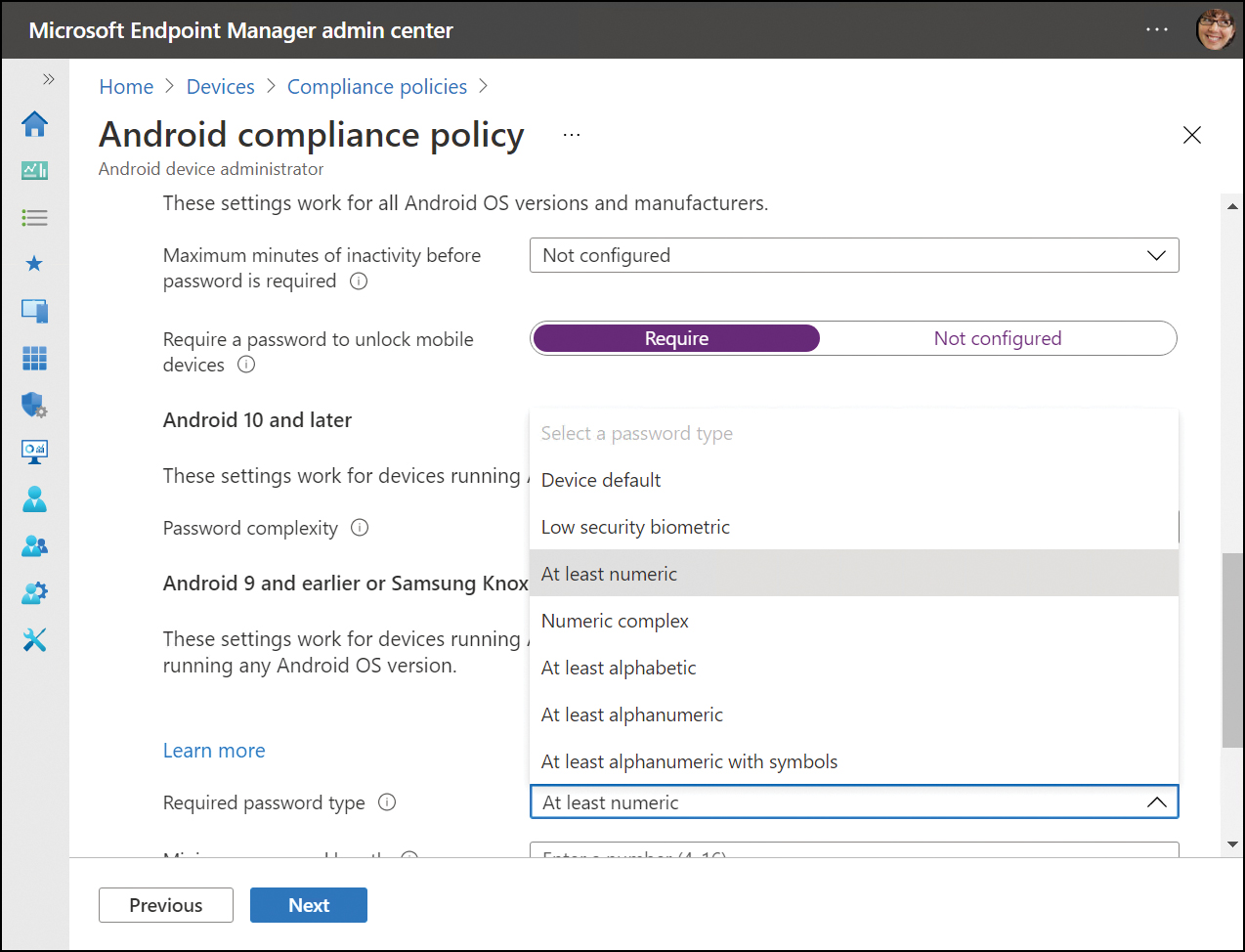
Figure 2-3 Configure Android compliance policy
Type 6 in the Minimum password length dialog box.
Review the remaining security settings.
Click Next three times, and then on the Assignments tab, choose the Android device or device group to assign the policy to, click Select, and then select Next.
Select Create to create the policy.
When you’ve successfully created the compliance policy and assigned it, the policy will appear in your list of device compliance policies.
Manage device compliance policies
Once you have created compliance policies within MDM, you can enforce the protection of your organizational data by requiring users and devices to meet business requirements. You have seen that the rules and settings available are extensive; when combined with conditional access, these rules and settings allow administrators to block users and devices that don’t meet the rules.
Whenever a device has a compliance policy assigned, a compliance status will be determined, as shown in Table 2-3.
TABLE 2-3 Compliance policy status
Status |
Severity |
|---|---|
Unknown |
1 |
NotApplicable |
2 |
Compliant |
3 |
InGracePeriod |
4 |
NonCompliant |
5 |
Error |
6 |
You can see that the severity increases when the device is in an error state or is noncompliant. The severity is reported to Microsoft Intune and is used when determining access to your organizational data.
When a device has multiple policies assigned, the device may have different compliance statuses. In these situations, Intune assigns a single resulting compliance status, which is based on the highest severity level of all the policies that are assigned to that device.
Policy refresh cycle times
Devices connect to Intune on a periodic basis and the compliance status is checked. The refresh cycle is the same as configuration profiles and can be found in Table 2-4. You will notice that if a device has been recently enrolled, the compliance check-in runs more frequently during this initial period.
TABLE 2-4 Compliance policy refresh cycle
Platform |
Initial Check-in Frequency |
Ongoing Refresh cycle |
|---|---|---|
iOS/iPadOS |
Every 15 minutes for 1 hour, and then every 8 hours |
8 hours |
macOS |
Every 15 minutes for 1 hour, and then every 8 hours |
8 hours |
Android |
Every 3 minutes for 15 minutes, then every 15 minutes for 2 hours, and then every 8 hours |
8 hours |
Windows 10 (enrolled as a device) |
Every 3 minutes for 15 minutes, then every 15 minutes for 2 hours, and then every 8 hours |
8 hours |
Windows 8.1 |
Every 5 minutes for 15 minutes, then every 15 minutes for 2 hours, and then every 8 hours |
8 hours |
If users open the Company Portal app on their device, they can sync the device to immediately check for new or updated policies. The Company Portal app also shows the compliance status of the managed device. For scenarios that include urgent compliance actions, such as Wipe, Lock, Passcode Reset, New App Deployment, New Profile Deployment, or New Policy Deployment, Intune will immediately notify the devices to perform a sync.

 Exam Tip
Exam Tip