Introduction to Azure Security Center
- By Yuri Diogenes and Tom Janetscheck
- 5/30/2021
- Deployment scenarios
- Understanding Security Center
- Planning adoption
- Onboarding resources
- Inventory
Planning adoption
Although Security Center is a cloud service, which means you don’t really need to deploy any server on-premises, there are still some aspects around the adoption that you should take into consideration. One of the most critical areas is to determine who should have access to Security Center. Depending on the size and structure of your organization, multiple individuals and teams may use Security Center to perform different security-related tasks.
Roles and permissions
Security Center uses Role-Based Access Control (RBAC) based in Azure. By default, there are two roles in Security Center: Security Reader and Security Admin. The Security Reader role should be assigned to all users that need read access only to the dashboard. For example, security operations personnel that need to monitor and respond to security alerts should be assigned the Security Reader role. It is important to mention that the assignment of this role is done at the Azure level, under the resource group that Security Center is monitoring, and using Access Control (IAM), as shown in Figure 2-5.
FIGURE 2-5 Access control in Azure
Workload owners usually need to manage a particular cloud workload and its related resources. Besides that, the workload owner is responsible for implementing and maintaining protections in accordance with company security policy. Because of those requirements, it would be appropriate to assign the Security Admin role to users who own a workload.
Centralized management
Large organizations that have different business units and are adopting Azure in a non-cohesive way might find challenges when trying to adopt Security Center because they don’t have visibility of all subscriptions that are part of their tenant. For this reason, even before enabling Security Center, you need to work with your IT Team to identify all subscriptions that belong to the tenant and verify whether you have the right privileges to manage Security Center. In some scenarios, the same company might even have multiple tenants with different subscriptions on each tenant.
When multiple subscriptions are part of the same tenant and you need to centralize policy across subscriptions, you can use Azure management groups. By aggregating multiple subscriptions under the same management group, you can create one role-based access control (RBAC) assignment on the management group, which will inherit that access to all the subscriptions. This saves time on management because you can enable users to have access to everything they need instead of scripting RBAC across different subscriptions. Security Center also supports to assign security policy to a management group.
If you plan to use centralized policy management with a management group, we recommend that you remove the ASC Default initiative from the subscription since the initiative will be inherited from the management group. You can use the instructions from this article to automate this process: http://aka.ms/ascbookmg.
When planning your Security Center adoption, make sure to determine what needs to be monitored and whether the default policy provided by Security Center is enough for your organization or if you need to create new definitions. You will learn more about security policies in Chapter 3, “Policy management.”
Storage
As explained previously, the agent will be collecting information and sending it to the workspace. If you are using Azure Defender for Server, you have up to 500 MB per day per node, and after that, Log Analytics charges will apply.
When planning Security Center adoption, consider the fact that workspaces that were created by Security Center have the data retained for 30 days. For existing workspaces, retention is based on the workspace pricing tier.
Recommendations
Security Center will identify resources (compute, network, storage, identity, and application) that need security recommendations, and will automatically suggest changes. You can see all recommendations in a single place, which is available by choosing General > Recommendations. There, you have all security controls, as shown in Figure 2-6. You just need to open each security control to see the recommendations for that security control. Another option is to set the option Group By Controls to Off and see the list of all recommendations. When planning your Security Center adoption, make sure to review all recommendations before exploring more capabilities in Security Center. You should use Security Center’s Secure Score impact to prioritize which security controls you should be addressing first. You will learn more about Secure Score in Chapter 4, “Strengthening your security posture.”
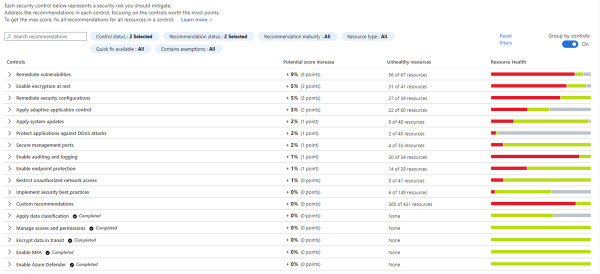
FIGURE 2-6 Aggregation of all security controls that contain recommendations in Security Center
Automation
Security Center deployment and configuration can be automated using Azure Resource Manager (ARM) templates, and PowerShell. In Chapter 10, “Deploying Azure Security Center at scale,” you will learn more about the use of ARM templates for large deployments of Security Center. Later in this chapter, you will learn how to use PowerShell for task automation.
Incorporating Security Center into your security operations
It’s critical that your IT security and IT operations departments constantly collaborate to provide better protection, detection, and response. Security operations (SecOps) describes this support function. Many organizations already have a SecOps team dedicated to maintaining the security operations and a cloud security posture management (CSPM) team responsible to monitor the security posture of cloud workloads. Security Center has capabilities that can be leveraged by the SecOps team, as well as by the CSPM team.
Before using Security Center to monitor resources, you must review your organization’s SecOps process and identify how you can incorporate Security Center into your routine. Figure 2-7 shows the tasks performed by a typical security operations center (SOC), typical tasks for the CSPM team, and the set of Security Center features that can be leverage by these teams.
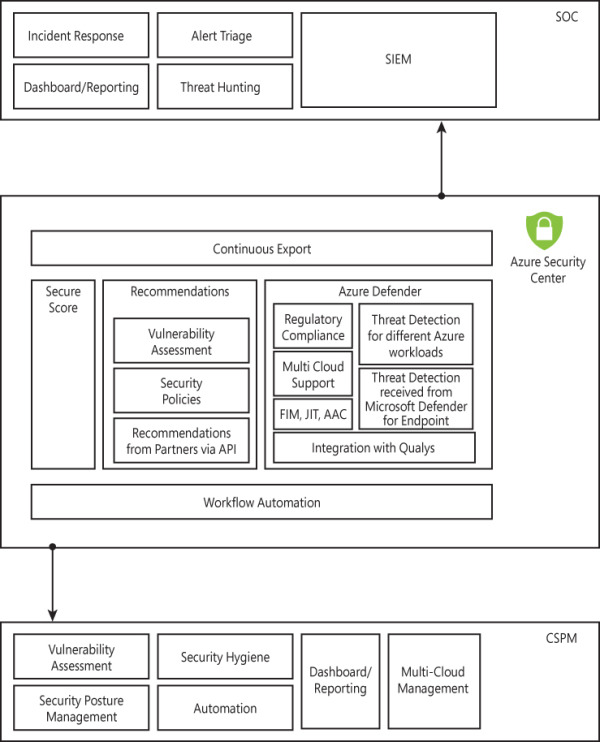
FIGURE 2-7 Mapping security operations and CSPM with Security Center
Here are a few key points for incorporating Security Center into your security operations and CSPM:
Security Center will continuously evaluate compute, network, storage, and application resources for compliance. The CSPM team is responsible for ongoing security assessment and should track and apply recommendations issued by Security Center on an ongoing basis. This team should also leverage Secure Score as their security Key.
Some of the capabilities that are related to CSPM, such as multi-cloud support, regulatory compliance, and Qualys integration for vulnerability assessment, will require you to upgrade your subscription to Azure Defender.
The security roles available in Security Center, along with Azure’s RBAC capability, can help SOC management control who has access to what part of the platform.
You can leverage Azure Monitor Workbooks to provide a specific level of visualization for the SOC Team. You can leverage some workbook samples available in the Azure Security Center community page, located at https://github.com/Azure/Azure-Security-Center/tree/master/Workbooks.
You should use the Workflow Automation feature for your CSPM team automated tasks. Make sure to leverage existing automations located on the Azure Security Center community page at https://github.com/Azure/Azure-Security-Center/tree/master/Workflow%20automation.
The SOC has its own incident response (IR) team, which can consume security alerts generated by Azure Defender threat detection via the Continuous Export feature.
SOC Analysts who are in charge of triaging alerts can also take advantage of Azure Defender Security Alerts dashboard to filter and suppress alerts. This team can also leverage the Workflow Automation feature to trigger response to specific alerts.
Another important consideration when incorporating Security Center as part of your SecOps is to establish how the data will be consumed by the team responsible for reviewing those alerts. Some organizations might already have a security information and event management (SIEM) system as part of their security operations, and they might not want to introduce another dashboard to their teams to query alerts. In this case, it is very common that you need to export Security Center alerts to their SIEMs by using the Continuous Export feature. In Chapter 8, “SIEM Integration,” you will learn how to perform this operation.
