The threat landscape
- By Yuri Diogenes and Tom Shinder
- 10/5/2019
- Understanding cybercrime
- Understanding the cyber kill chain
- Cloud threats and security
- Azure Security
Cloud threats and security
As explained at the beginning of this chapter, cloud weaponization is happening, and current data exposed in the Microsoft Security Intelligent Report Volume 22 shows the global outreach of these attacks. According to these reports, more than two-thirds of incoming attacks on Azure services in the first quarter of 2017 came from IP addresses in China (35.1%), the United States (32.5%), and Korea (3.1%). The remaining attacks were distributed in 116 other countries and regions. Sometimes, threat actors will weaponize the cloud to send an attack to a target system, as shown in Figure 1-4. Other times, attackers will simply hijack resources of the target system.
Cryptomining is a rising threat, and when you combine this with the elasticity of cloud computing, you have the perfect storm. Let’s say a cloud admin misconfigured a Kubernetes, or a Docker registry, this misconfiguration exposed the system to allow free public access to it. Attackers could deploy containers that will mine crypto.
The weaponization of the cloud resources to attack a different target system is shown in Figure 1-4. This diagram represents an attacker gaining access to VMs located in the cloud and leveraging compute resources from this VMs to attack on-premises assets. This is a typical cloud weaponization scenario.
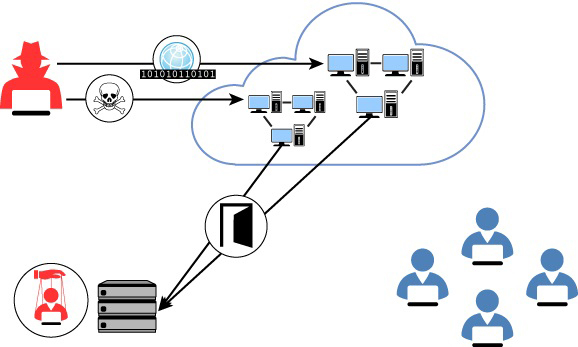
FIGURE 1-4 Cloud weaponization targeting on-premises resources
Another potential threat in the cloud happens because of flaws in configuration and DevOps. One common scenario is the public key secret shared in a public cloud. An event like that happened in 2015 when bots were scanning GitHub to steal Amazon EC2 keys. The diagram shown in Figure 1-5 illustrates a similar scenario.
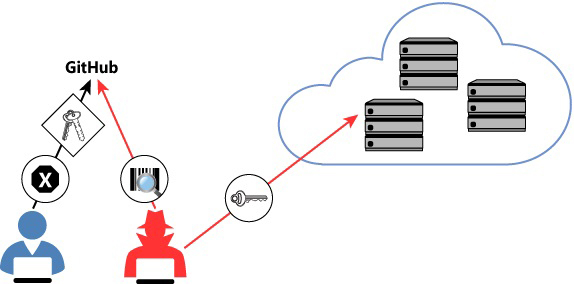
FIGURE 1-5 Public secret attack scenario
Attackers are also shifting efforts to evade detections provided by Cloud Workload–Protection Platforms. In January 2019, a report from Palo Alto Networks showed how a malware used by the Rocke group developed a capability to uninstall the CWPP agent before the malware began showing signs of malicious behavior. Cloud Providers must act quickly to remediate scenarios like this, and when you are selecting your CWPP, you need to be aware of how quickly those CWPPs can respond to new threat vectors like this.
For this reason, it is imperative that before adopting cloud computing, organizations must first understand the security considerations that are inherited by the cloud computing model. These considerations must be revised before adopting—ideally during the planning process. Without a full understanding of cloud security considerations, the overall successful adoption of cloud computing may be compromised.
Consider the following areas for cloud security:
Compliance
Risk management
Identity and access management
Operational security
Endpoint protection
Data protection
Each one of these areas must be considered; some areas can be explored in more depth than others, depending on the type of business that you are dealing with. The sections that follow describe each of these scenarios in more detail.
Compliance
During the migration to the cloud, organizations need to retain their own compliance obligations. These obligations could be dictated by internal or external regulations, such as industry standards that they need to be compliant with in order to support their business models. Cloud providers must be able to assist customers to meet their compliance requirements via cloud adoption.
In many cases, cloud solution providers (CSP) will become part of the customer’s chain of compliance. Consider working closely with your cloud provider to identify your organization’s compliance needs and verify how the provider can fulfill your requirements. It is also important to verify whether the CSP has a proven record of delivering secure and reliable cloud services while keeping customers’ data private and secure.
Ideally, your Cloud Security Posture Management (CSPM) platform will enable you to map the security controls that are applied to your cloud workloads to major regulatory compliance standards.
Risk management
Cloud customers must be able to trust the CSP with their data. CSPs should have policies and programs in place to manage online security risks. These policies and programs may vary depending on how dynamic the environment is. Customers should work closely with CSPs and demand full transparency to understand risk decisions, how these risks vary depending on data sensitivity, and the level of protection required.
Identity and access management
Organizations planning to adopt cloud computing must be aware of the identity- and access-management methods available and of how these methods will integrate with their current on-premises infrastructures.
These days, with users working on different devices from any location and accessing apps across different cloud services, it is critical to keep the user’s identity secure. Indeed, with cloud adoption, identity becomes the new perimeter—the control panel for your entire infrastructure, regardless of the location, be it on-premises or in the cloud. You use the user’s identity to control access to any services from any device and to obtain visibility and insights into how your data is being used.
As for access management, organizations should consider auditing and logging capabilities that can help administrators monitor user activity. Administrators must be able to leverage the cloud platform to evaluate suspicious log-on activity and to take preventive actions directly from the identity-management portal.
Operational security
Organizations migrating to the cloud should evolve their internal processes—security monitoring, auditing, incident response, and forensics—accordingly. The cloud platform must enable IT administrators to monitor services in real time to observe the health conditions of these services and provide capabilities to quickly restore services that were interrupted. You should also ensure that deployed services are operated, maintained, and supported in accordance with the service-level agreement (SLA) established with the CSP.
Endpoint protection
Cloud security is not only about the security of the CSP infrastructure; it is a shared responsibility. Endpoint protection is one aspect of security for which organizations are responsible. Organizations that adopt cloud computing should consider increasing endpoint security because these endpoints will be exposed to more external connections and will access apps that may be housed by different cloud providers.
Users are the main target of attacks, and endpoints are the devices employed by users. An endpoint might be a user’s workstation, a user’s smartphone, or any other device that can be employed to access cloud resources. Attackers know that the user is the weakest link in the security chain, and attackers will continue to invest in social-engineering techniques, such as phishing emails, to entice users to perform actions that can compromise an endpoint.
One important approach to enable the end-to-end visibility of your endpoint protection and your cloud workloads is the integration of your Cloud Workload Protection Platform (CWPP) with your Endpoint Detection and Response (EDR) solution.
Data protection
Regarding cloud security, the goal when migrating to the cloud is to ensure that data is secure no matter where it is located. Data might exist in any of the following states and locations:
Data at rest on the user’s device In this case, the data is located at the endpoint, which can be any device. You should always enforce data encryption at rest for company-owned devices and in BYOD scenarios.
Data in transit from the user’s device to the cloud When data leaves the user’s device, you should ensure that the data is still protected. There are many technologies that can encrypt data regardless of its location—for example, Azure Rights Management. It is also imperative to ensure that the transport channel is encrypted. Therefore, you should enforce the use of Transport Layer Security (TLS) to transfer data.
Data at rest in the cloud provider’s datacenter When data arrives at the cloud provider’s servers, the CSP’s storage infrastructure should ensure redundancy and protection. Make sure you understand how your CSP performs data encryption at rest, who is responsible for managing the keys, and how data redundancy is performed.
Data in transit from the cloud to on-premises In this case, the same recommendations specified in the “Data in transit from the user’s device to the cloud” bullet apply. You should enforce data encryption on the file itself and encrypt the transport layer.
Data at rest on-premises Customers are responsible for keeping their data secure on-premises. Encrypting at-rest data at the organization’s datacenter is a critical step to accomplish this. Ensure that you have the correct infrastructure to enable encryption, data redundancy, and key management.
