Using Security Center for incident response
- By Yuri Diogenes and Tom Shinder
- 8/23/2018
Detection scenarios
There are many scenarios in which Security Center will rapidly warn you about a suspicious activity. The following sections cover a couple of important scenarios to give you an idea of how powerful Security Center detections are and the advantage of using multiple data sources to enhance the confidence level of an alert.
Detecting spam activity
In this detection scenario, the attacker compromises an Azure VM and uses it to send spam emails. Using machine learning, Security Center can detect a spike in SMTP traffic. It then queries other data sources to make sure this spike is due to malicious behavior. Finally, it correlates this traffic with the Office 365 spam database to determine whether it is legitimate traffic. If the result of this correlation is that the traffic is suspicious, Security Center triggers the alert shown in Figure 5-1. In this scenario, Security Center uses built-in analytics, machine learning, and threat intelligence from Office 365. Performing these three steps provides not only more precise detection but also a higher level of confidence in the alert.
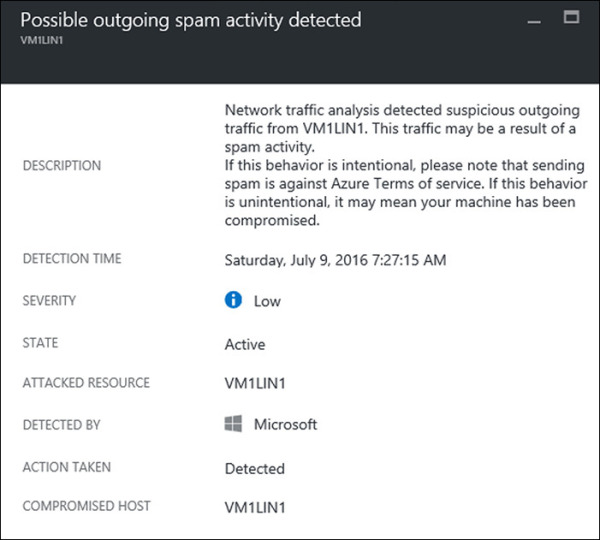
FIGURE 5-1 Spam alert in Security Center.
Crash-dump analysis
In this scenario, the attacker compromises an Azure VM and installs malware that goes undetected by the antimalware installed on the VM. This malware causes a crash in a legitimate program. When a crash occurs in a Windows system, Windows Error Reporting (WER) generates a user-mode memory crash dump (.dmp file), which by default is located under %LOCALAPPDATA%\CrashDumps. Security Center collects an ephemeral copy of the crash dump file and scans it for evidence of exploits and compromises.
If Security Center finds such evidence, it generates an alert like the one shown in Figure 5-2. This alert indicates that the crash-dump analysis has detected executable code that exhibits behavior that is commonly performed by malicious payloads. Although non-malicious software may perform this behavior, it is not a typical development practice. Follow the remediation steps to investigate this issue further.

FIGURE 5-2 Crash-dump analysis alert.
