The threat landscape
- By Yuri Diogenes and Tom Shinder
- 10/5/2019
- Understanding cybercrime
- Understanding the cyber kill chain
- Cloud threats and security
- Azure Security
Understanding the cyber kill chain
One of the most challenging aspects of defending your systems against cybercriminals is recognizing when those systems are being used for some sort of criminal activity in the first place—especially when they are part of a botnet. A botnet is a network of compromised devices that are controlled by an attacker without the knowledge of their owners. Botnets are not new. As a matter of fact, a 2012 Microsoft study found that cybercriminals infiltrated insecure supply chains using the Nitol botnet, which introduced counterfeit software embedded with malware to secretly infect computers even before they were purchased. (For more information, see https://aka.ms/nitol.)
The best way to prevent this type of attack, or any other, is to identify attack vectors—that is, how an attacker will attack your environment. To help with this, Lockheed Martin developed a cyber kill chain. Each step in this chain represents a particular attack phase. (See Figure 1-1.)
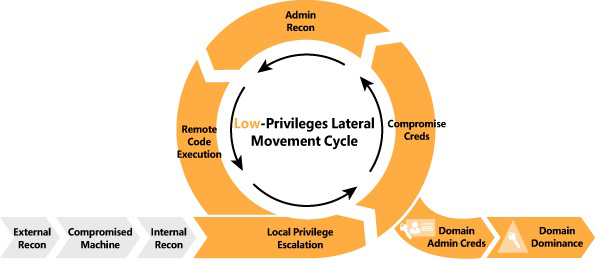
FIGURE 1-1 Example of the cyber kill chain steps
The steps in this chain are as follows:
External recon During this step, attackers typically search publicly available data to identify as much information as possible about their targets. The goal of this step is to obtain intelligence, or intel, to better perform the attack and increase the likelihood of success.
Compromised machine During this step, attackers leverage different techniques, such as social engineering, to entice users to do something. For example, the attacker might send a phishing email to lure the user into clicking a link that will compromise the machine. The goal is to establish a foothold on the victim’s network.
Internal recon and lateral movement During this step, the attacker performs host discovery and identifies and maps internal networks and systems. The attacker may also start moving laterally between hosts, looking for a privileged user’s account to compromise.
The low-privileges lateral movement cycle During this cycle, the attacker continues to search for accounts with administrative privileges so that he or she can perform a local privilege escalation attack. This cycle typically continues until the attacker finds a domain administrative user account that can be comprised.
Domain admin creds At this point, the attacker needs complete domain dominance. To achieve this, the attacker will pivot through the network, either looking for valuable data or installing ransomware or any other malware that can be used for future extortion attempts.
Common threats
As mentioned, one common type of attack is the use of drive-by download sites. These are websites that host one or more exploits that target vulnerabilities in web browsers and browser add-ons. According to the Microsoft Security Intelligence Report, Volume 22, Bing detected 0.17 drive-by download pages for every 1,000 pages in the index in March 2017.
According to the same report, in the first quarter of 2017, trojans were the most commonly encountered type of malicious software (followed by worms and droppers). Trojans always pose as a useful application. For example, take the Win32/Xadupi Trojan, also called WinZipper (%ProgramFiles%\WinZipper\) or QKSee (%ProgramFiles%\qksee\). In addition to creating a shortcut to itself in the Start menu (see Figure 1-2) that enables users to zip and unzip files, this Trojan also creates a service (qkseeService) that connects to command and control (C2) servers and periodically checks for instructions using HTTP requests. Often, these instructions silently download new files, which could contain malware that will be executed on the local computer. This is just one example of how threats spread.
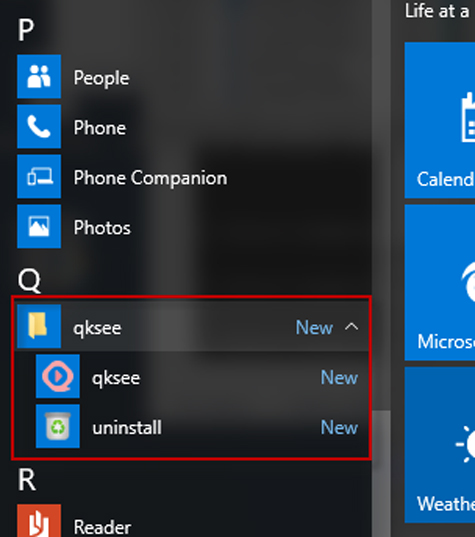
FIGURE 1-2 Typical installation location for QKSee
These days, the user is almost always the target because he or she is the weakest link. With the proliferation of mobile devices, bring-your-own-device (BYOD) models, and cloud-based apps, users are installing more and more apps. All too often, these apps are merely malware masquerading as valid apps. Many do something similar to (or even worse than) what QKSee does. For this reason, it is important to have good endpoint protection as well as a detection system that can look across different sources to intelligently identify unknown threats by leveraging cutting-edge technologies, such as analytics and machine learning.
Building a security posture
At one time, cybersecurity experts recommended that organizations simply invest more in protecting their assets. Today, however, simply investing in protecting your assets is not enough. Instead, organizations should invest in building a solid security posture. As shown in Figure 1-3, a security posture is composed of three major pillars.
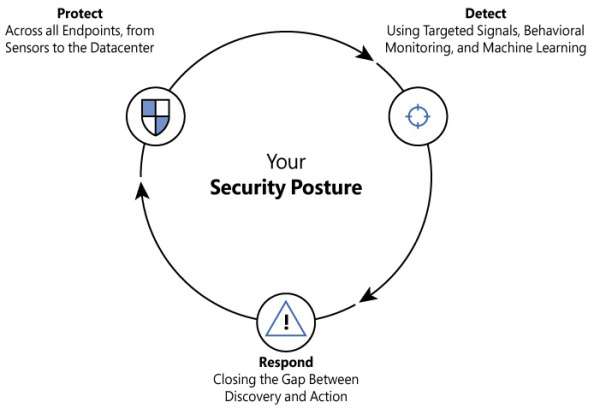
FIGURE 1-3 The three pillars of your security posture
According to the InfoSec Institute, attackers lurk on networks for an average of 200 days without being detected. (See http://resources.infosecinstitute.com/the-seven-steps-of-a-successful-cyber-attack for more information.) No doubt, this is a huge amount of time to have an attacker inside your network. However, the key word here is detected. Without a good detection mechanism, you have no way to disrupt an attack. Hence, it is imperative to invest in a holistic solution to monitor cloud-based resources as well as on-premises assets. You must be able to quickly detect an attack and to use actionable data to improve your response. All that being said, collecting data without analyzing it only delays the response process. That’s why it is so important to use tools that leverage technologies such as behavior analytics, threat intelligence, and machine learning for data correlation. Azure Security Center will do all that for you, and it will reduce false positives and show what’s relevant for you to proceed with your investigation.
Assume breach mentality
Microsoft recognizes the fact that preventing a breach is not enough. Microsoft haven’t “given up” or “thrown up the white flag” and continue to use all the traditional prevent-breach processes and technologies. However, in addition to those, we realize that we must do more. That “more” is encompassed by a philosophy of “assume breach.” An assume-breach mentality means that while we hope that we will never be breached, we know that hope is a poor strategy. Therefore, we assume that our public cloud network is about to be breached—or has already been breached—and then come up with people, processes, and technology that will help us find out when the breach occurred as early as possible, discover which breach occurred, and then eject the attacker with the goal being to limit expansion of the breach as much as possible.
We use the assume breach approach to help us understand how attackers gain access to the system and then develop methods that enable us to catch the attacker as soon as possible after the breach takes place. Because attackers typically enter a system via a low-value target, if we can detect quickly when the target has been compromised, we can block the attacker from expanding outward from the low-value asset to higher-value assets. These high-value assets are the attacker’s ultimate target.
How do we do this? One very effective method we use is red teaming or red/blue team simulations. In these exercises, the red team takes on the role of the attacker, and the blue team takes on the role of defender. We define the parameters of the exercise. Then, for the agreed-upon duration of the exercise, the red team tries to attack the Azure infrastructure and the Blue Team tries to discover what the Red Team has done and attempts to block the red team from compromising addition systems. (Of course, the blue team’s goal is to thwart the red team’s attempts to compromise the blue team’s systems).
At the end of the exercise, the red and blue teams discuss what happened. Specific topics to discuss include
How the red team might have gotten in;
How the blue team discovered and ejected the red team;
New technologies and operational procedures that make discovering comprised systems faster and easier.
